Hello readers.
This time I’ve found a quite interesting vulnerability in the widely spread firewall appliance “Astaro Security Gateway” (ASG) which is now maintained by Sophos.
Although it only has got an assigned CVSSv2 Score of 3,5 (AV:N/AC:M/Au:S/C:N/I:P/A:N), it offers some possibilities to a remote attacker. Due to an improper input validation on the “Comment (optional)” input field, an attacker is able to permanently inject own – probably malicious – JavaScript / HTML code into the WebAdmin Backup-view:
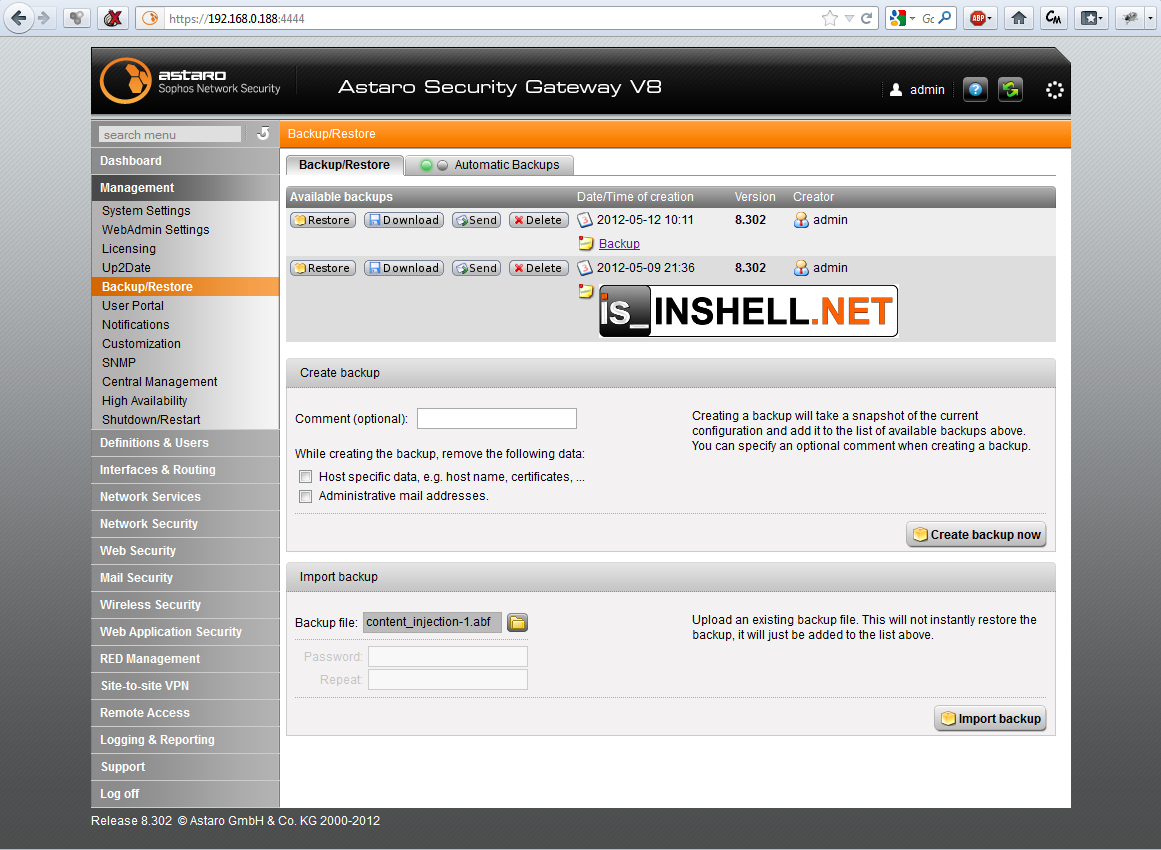
Which could lead to cookie theft, session highjacking, server side context manipulation or further browser exploitation. Ok so far. BUT! Why should an attacker who has already got access to the WebAdmin of the ASG manipulate the content of the firewall ? That’s not usable at all. The bad part about this vulnerability is, that the comment is automatically included into the created backup-file:
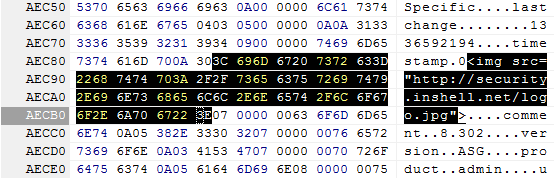
Now this offers the possibility to remotely modify the WebAdmin interface of the ASG by getting the victim to upload an arbitrary/manipulated backup-file into his ASG – exploit the human using some social engineering ;-). And the victim does not need to apply the backup file, the plain import is enough to exploit this vulnerability.
Administrators should update to the latest available version v8.305 where the issue has been fixed by Sophos._
All in all Sophos did a great Job on this security issue! I’ve reported the vulnerability to Sophos on 2012-05-11 and received a response only 20 minutes after my first notification. After the initial communication I got in contact with Mr. Hennig (CTO of Astaro/Sophos) who did the further communication with me – always professional, always friendly and this is why working on security issues together motivates! Thank you!
Another thing to mention: This is my first public advisory release which includes a CVE identifier, which I’ve requested from MITRE :-). I’m going to include a CVE identifier in all my future advisories as long as they’re interesting enough.
The full advisory can be found here: http://security.inshell.net/advisory/27
