Great news from the vulnerability front! I’m happy to see that the quality of vulnerability coordination with Watchguard evolved to my satisfaction during the past few months and the following new vulnerability disclosure proves that. Reported –> ACK’ed –> bypassed –> fixed –> Update v 11.8 released, which fixes the XSS issues!
The vulnerabilities are standard Cross-Site Scripting issues resulting in non-persistent context manipulation, session hijacking and finally account-theft.
A typical exploit looks like that:
https://192.168.0.34:4130/log/device?sn=random&cluster_id=&l_t=tr&name=<script>alert(document.cookie)</script>
resulting in:
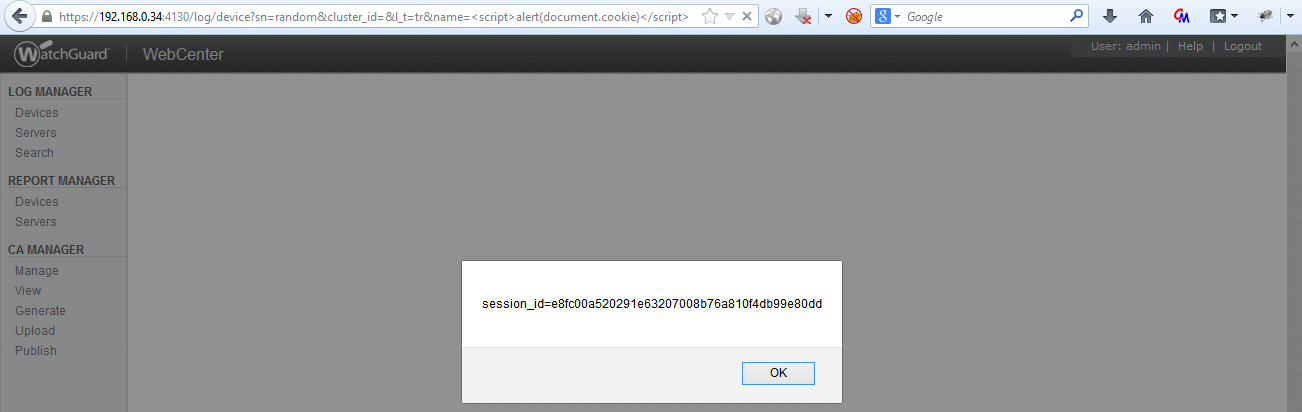
Two interesting facts:
- Looks like the serial number is a possible mitigation factor, which makes it harder for an attacker to exploit the vulnerability. But… No – he does not need to know the serial number! The GET parameter “sn” can contain any random value, but mustn’t be empty.
- These XSS issues are authenticated vulnerabilities with the “advantage” (in this case) of not being executed when the victim clicks on the link: if the victim is currently not logged into the Watchguard Server Center, he is redirected to the login page, that carries the payload in another GET parameter “from_page”:
https://192.168.0.34:4130/auth/login?from_page=/log/device%3Fsn%3Drandom%26cluster_id%3D%26l_t%3Dtr%26name%3D%253Cscript%253Ealert%28document.cookie%29%253C/script%253E
and after the successful login, the script code is rexecuted – leading to session_id theft.
The official Full-Disclosure post can be found here and the official Watchguard statement can be found here.
